- 8777701917
- info@saikatinfotech.com
- Basirhat W.B


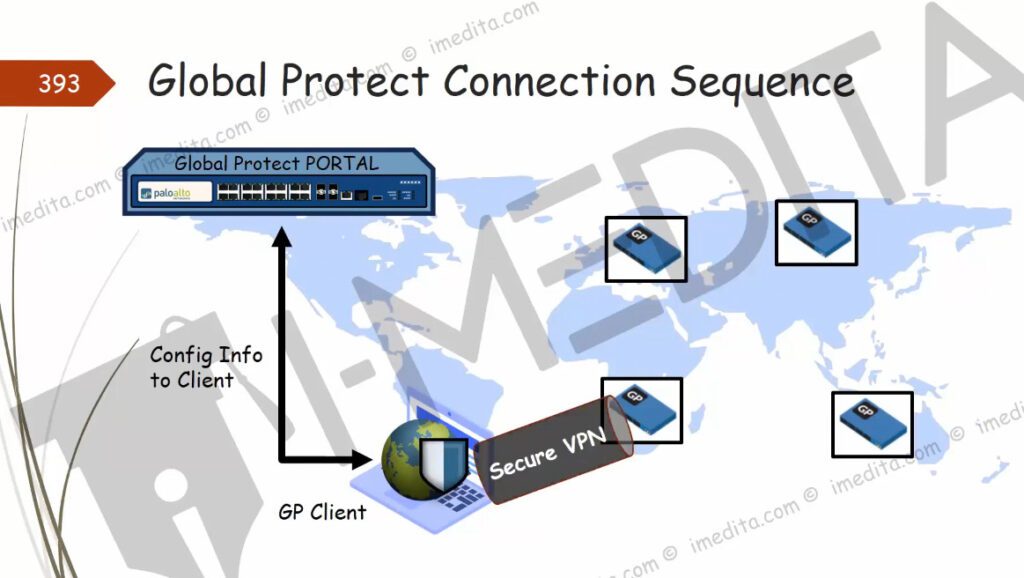

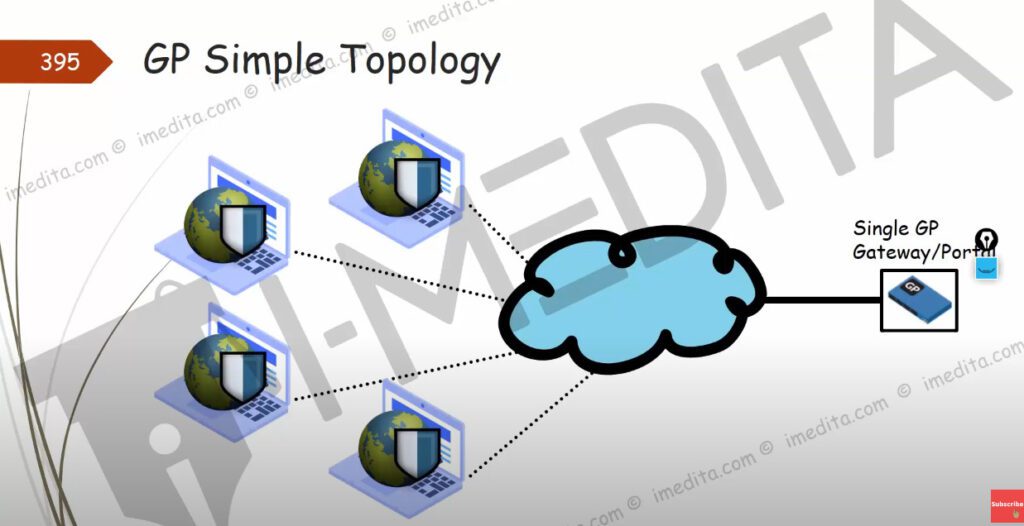
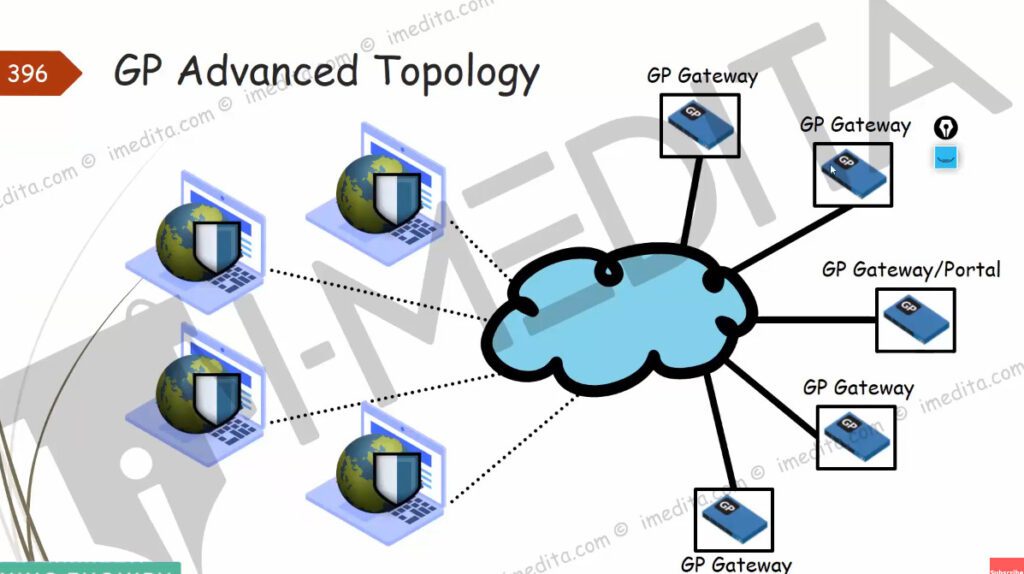





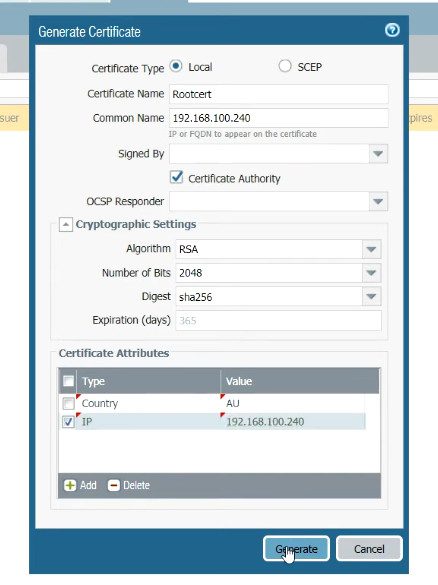
Step 1.Generating a Self-Sign Certificate for GlobalProtect.
Click on Device >> Certificate Management >> Certificates >> Device Certificates >> Generate. Now, just fill the Certificate filed as per the instruction appears on screen.
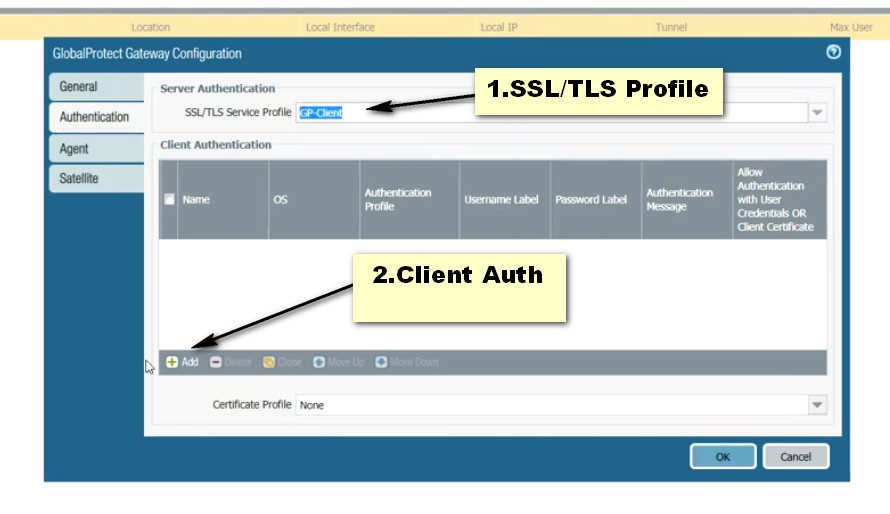
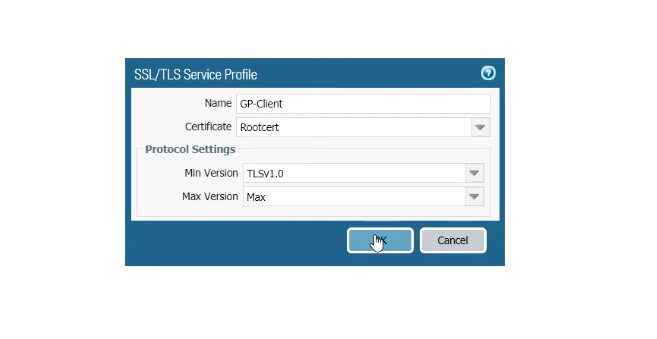
Step 2. Creating an SSL/TLS Service Profile.
Click on Device >> Certificate Management >> SSL/TLS Service Profile >> Add. Select the certificate of TLS.
Step 3. Creating Local Users for GlobalProtect VPN Authentication.
Click on Device >> Local User Database >> Users and click on Add.

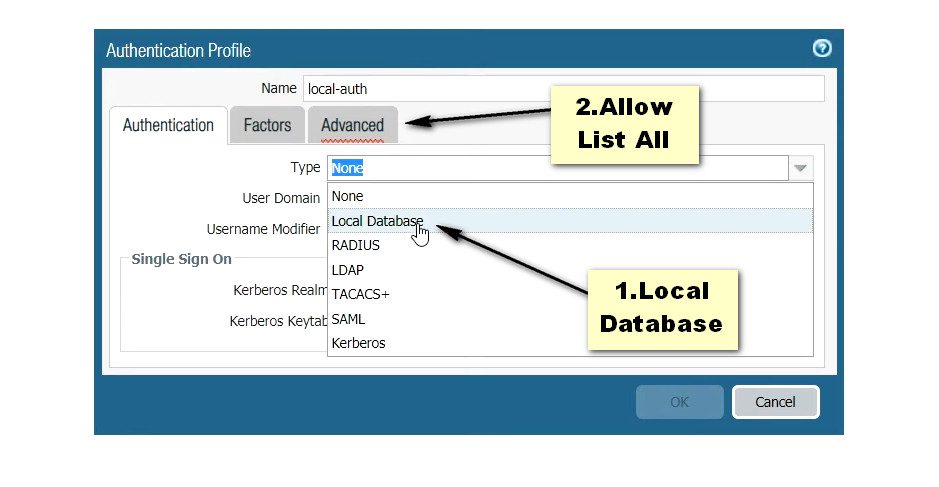
Step 4. Creating Authentication Profile for GlobalProtect VPN.
Click on Device >> Authentication Profile and click on Add. Open the Advanced tab and add users to Allow List.
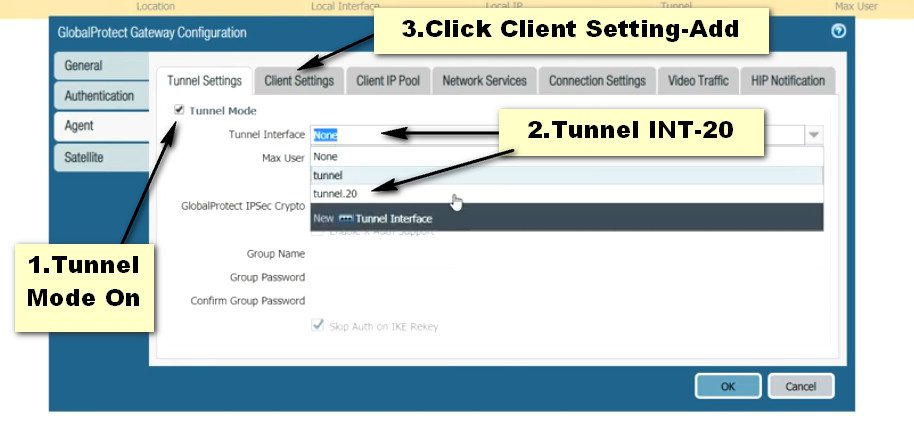
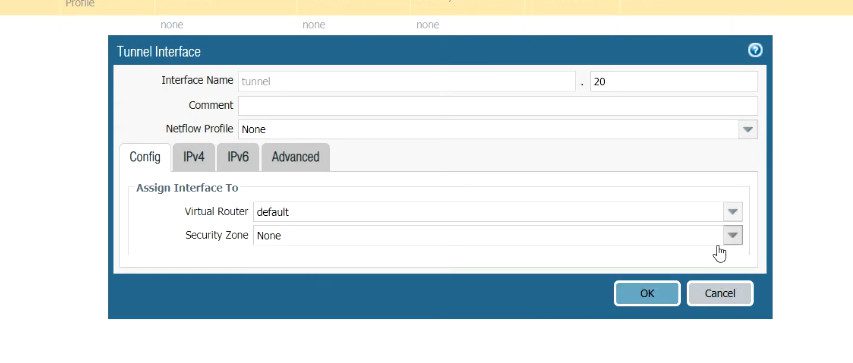
Step 5. Creating a tunnel interface for GlobalProtect.
Click on Network >> Interfaces >> Tunnel >> Add, to create a tunnel interface.
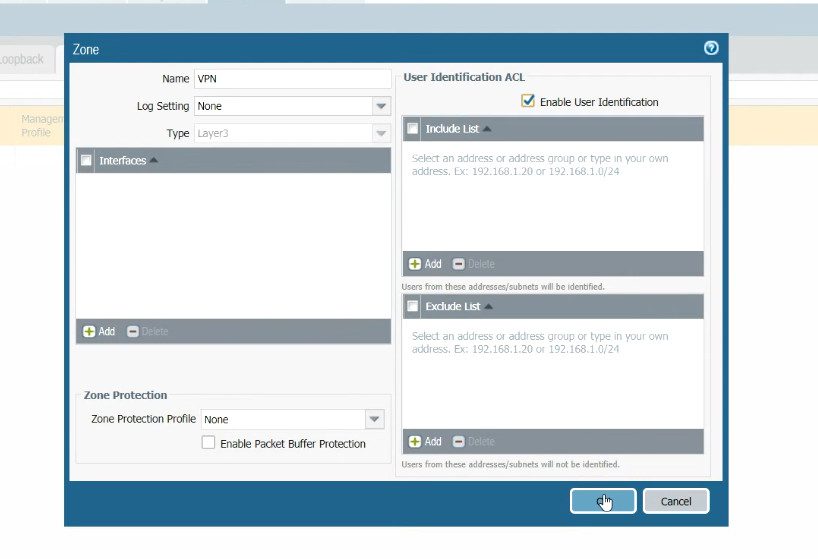
Step 5. Creating a zone for GlobalProtect VPN Traffic.
To create Security Zone, click on Network >> Zones >> Add.
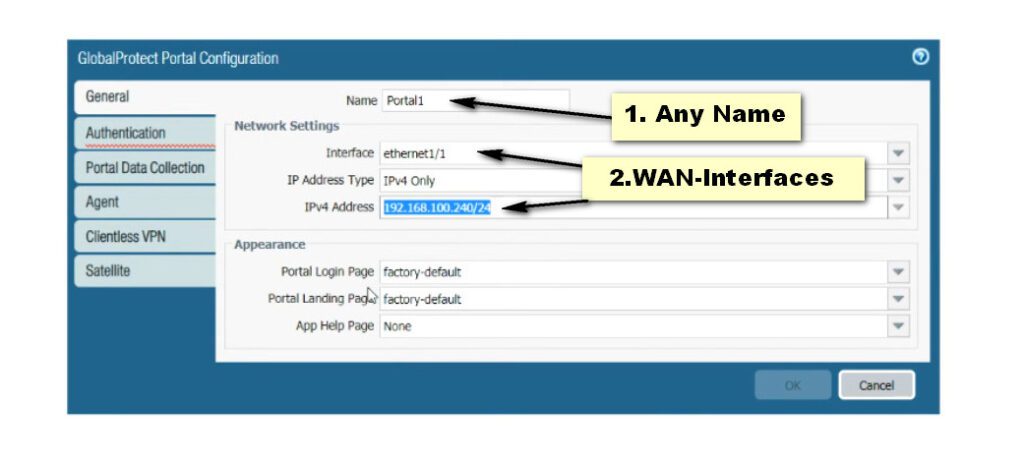
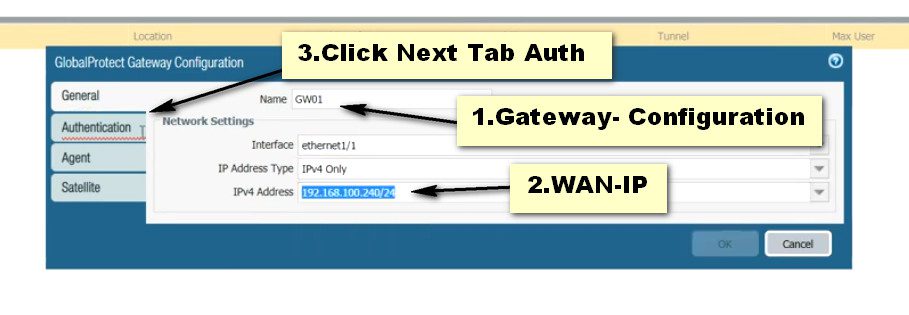
Step 7. Portal Configuration for GlobalProtect.
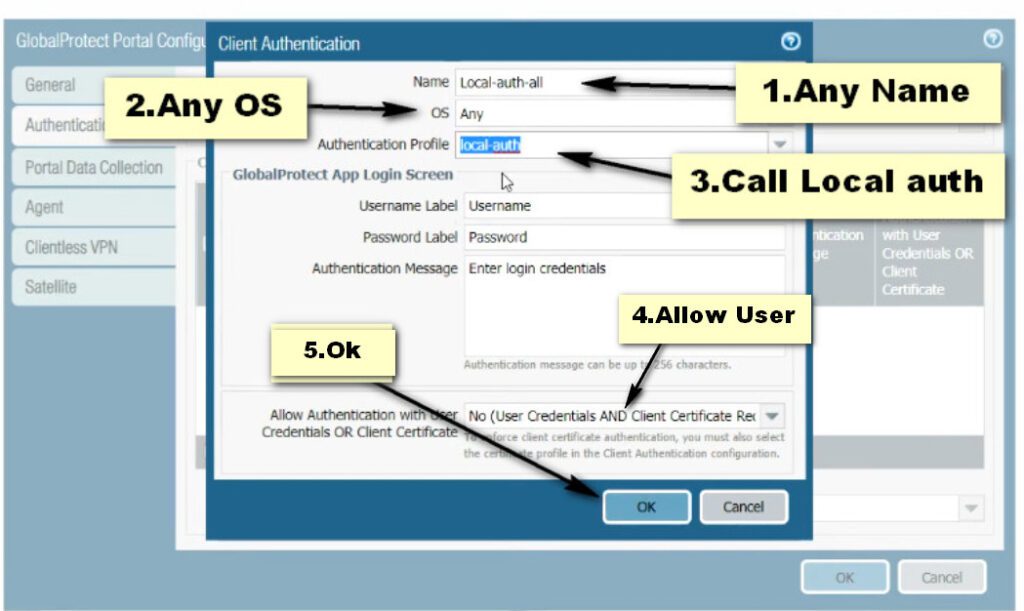
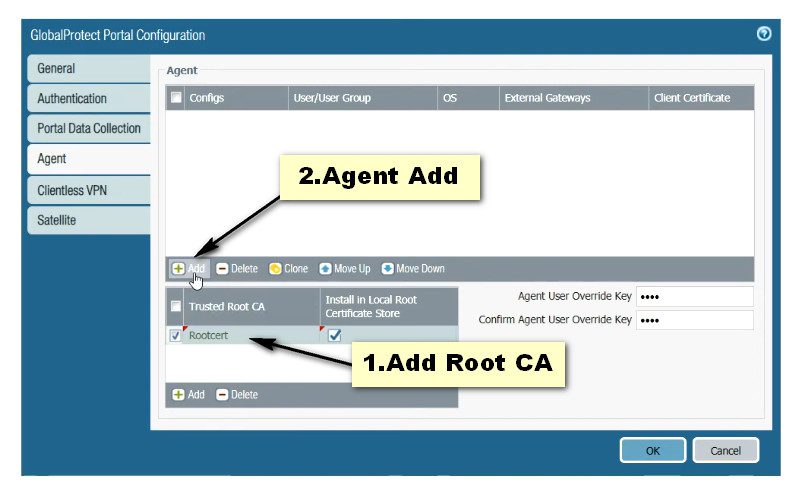
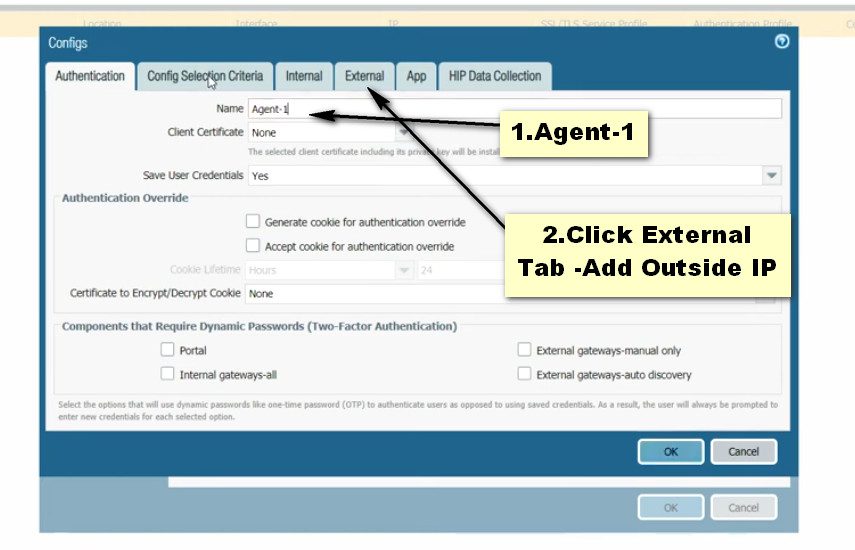
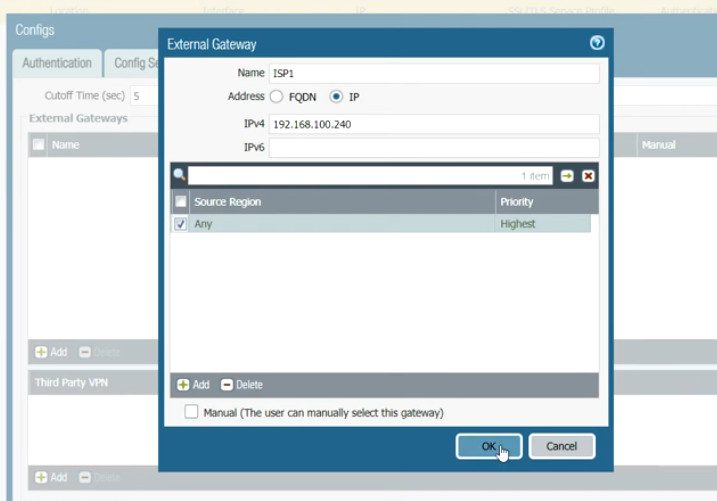
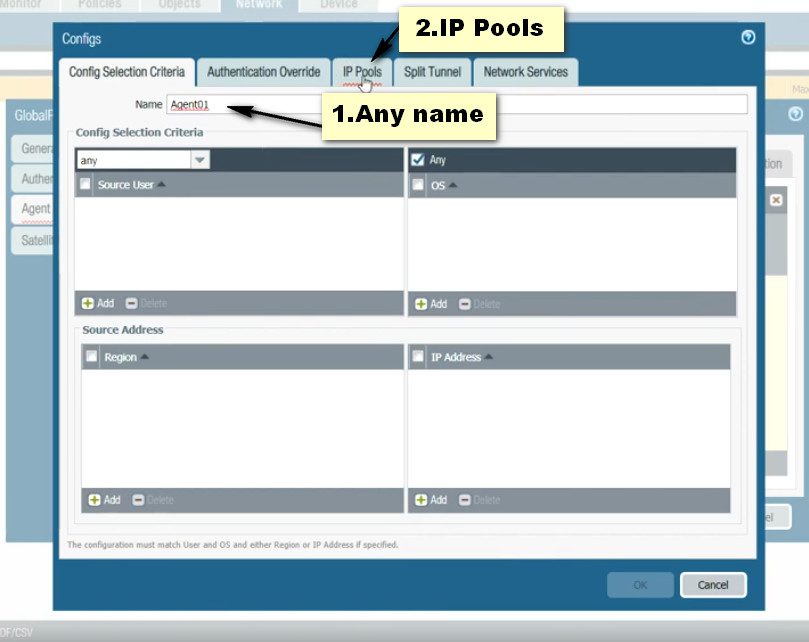
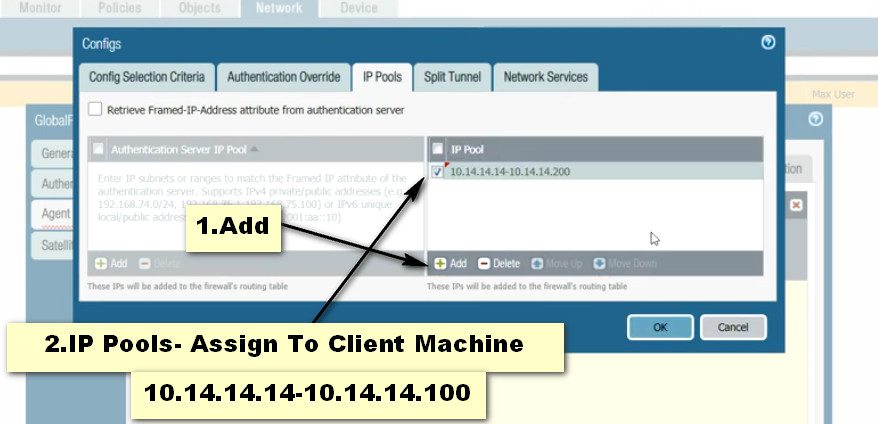
Click on the GlobalProtect >> Portals >> Add. Open the General tab and Provide the name for GloablProtect Portal Configuration. Open the Authentication Tab, open the SSL/TLS service profile which you are created in Step 2. In Client Authentication, click on ADD. Now, Open the Agent tab, and select the Trusted Root CA (created in Step 1) and check the option “Install in Local Root Certificate Store” Open the User/User Group tab and choose OS and User/User Group you have on your environment. Open the External tab and Add an External Gateway. Enter the Name to External Gateway and provide IP, Source Region and Priority details and click OK.