- 8777701917
- info@saikatinfotech.com
- Basirhat W.B
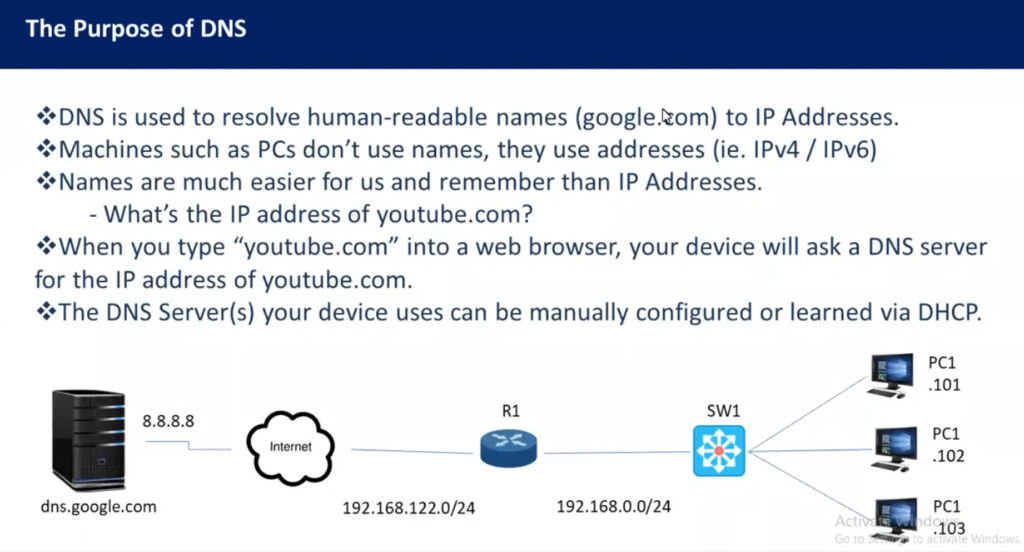
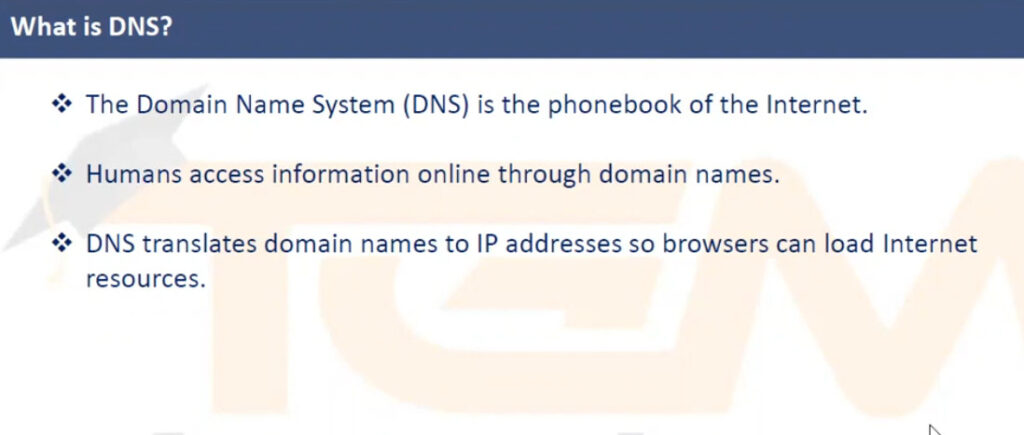
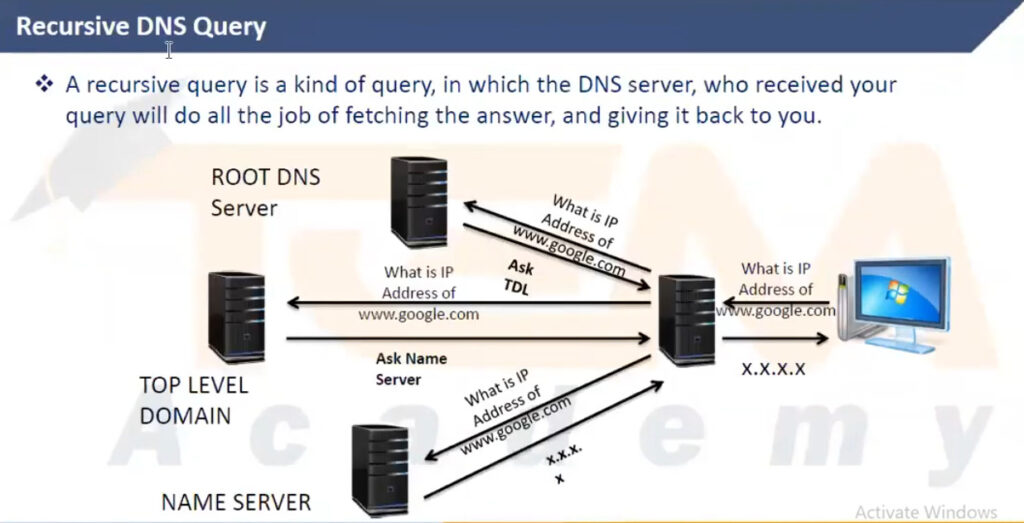
DNS stands for Domain Name System, and it is a fundamental part of how the internet works. It is often described as the “phonebook of the internet” because it translates human-readable domain names (such as www.example.com) into IP addresses (such as 192.0.2.1), which computers use to identify each other on the network.
When you enter a URL (such as www.example.com) in your web browser, your computer needs to know the IP address of the server that hosts that website in order to establish a connection. Since humans are better at remembering domain names than numerical IP addresses, DNS servers perform this translation.
For example:
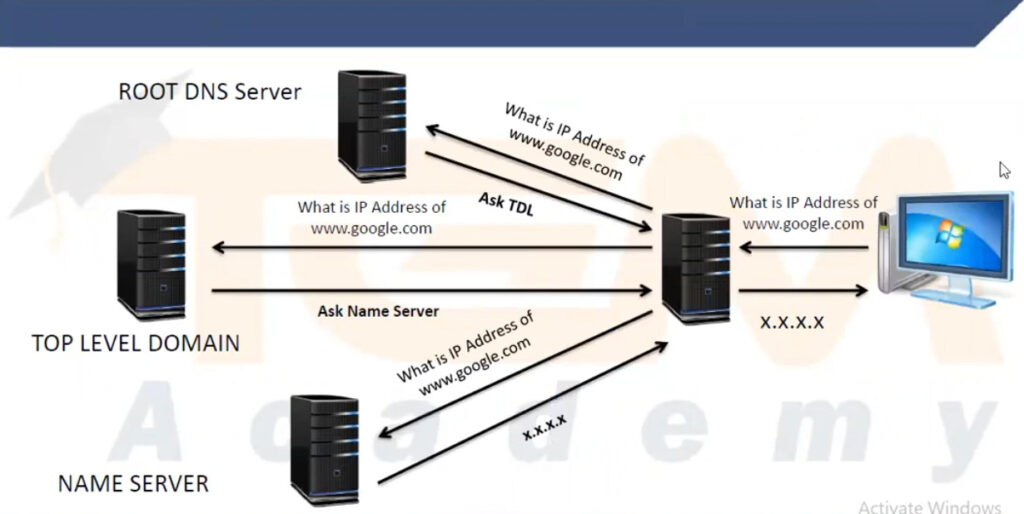
www.example.com in your browser.93.184.216.34.You type a domain name: When you enter a domain name in your browser (like www.example.com), the request is sent to your local DNS resolver (often provided by your internet service provider).
DNS resolver looks for the domain: If the IP address for that domain is already cached (stored locally from a previous query), the resolver will use it to connect to the website. Otherwise, the DNS resolver will start the process of querying other DNS servers.
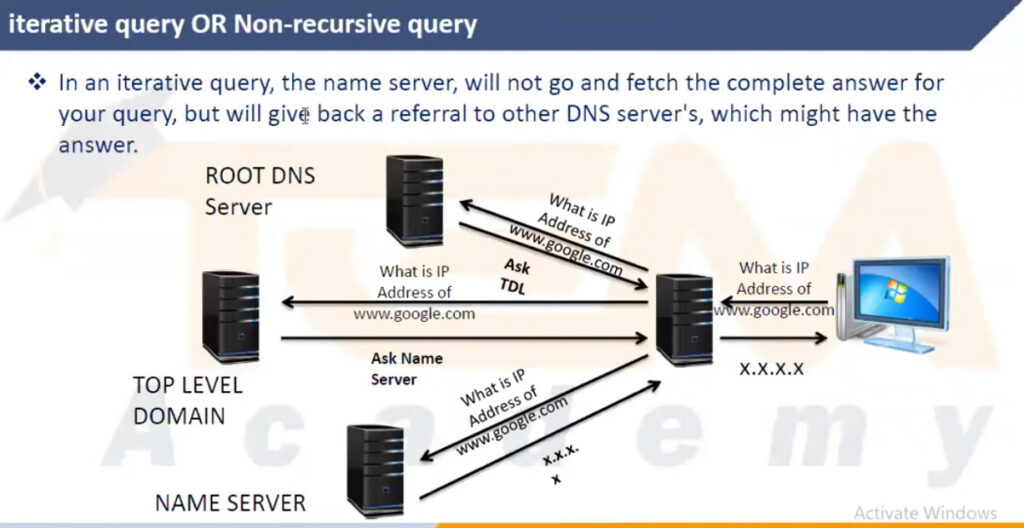
Recursive lookup begins: The resolver sends a query to the root DNS server, which doesn’t know the specific IP address but points the resolver to the Top-Level Domain (TLD) server (for example, .com, .org, .net).
TLD server response: The TLD server knows where to find the authoritative DNS server for the domain. For example, it may point the resolver to the authoritative name server for example.com.
Authoritative DNS server: This server is the final source of truth. It holds the actual IP address (or addresses) for www.example.com. The authoritative server responds with the IP address.
DNS response: The DNS resolver sends the IP address back to your computer, which then connects to the server hosting the website using that IP address.
Caching: To make this process more efficient, the DNS resolver and your computer will cache the IP address for a period of time (called the Time-to-Live, or TTL). This helps avoid having to repeat the lookup process each time the website is visited.
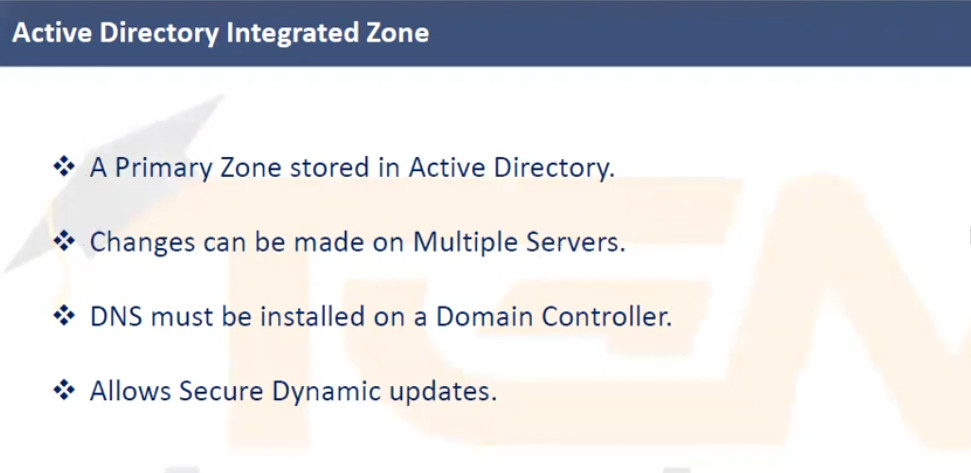
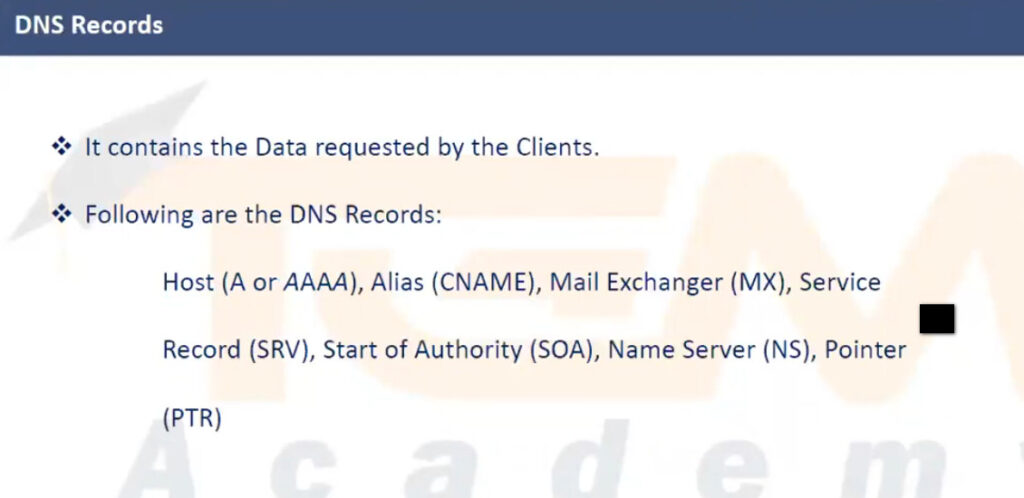
DNS Records: DNS records are the individual entries in the DNS database that map domain names to IP addresses or other resources. Some of the most common types of DNS records are:
DNS Server Types:
example.com.DNS Caching: DNS resolvers and local computers cache domain name lookups for a specified period of time to improve performance and reduce the load on DNS servers. Cached information is kept based on the TTL value set by the authoritative server.
www.google.com) instead of having to memorize numerical IP addresses.www.google.com) instead of IP addresses (like 172.217.15.78).Without DNS, navigating the web would be incredibly difficult since we’d have to rely on remembering numerical IP addresses instead of user-friendly domain names.
DNS records are used to store information about a domain, such as its associated IP addresses, mail servers, and other related data. Some of the most common types of DNS records include:
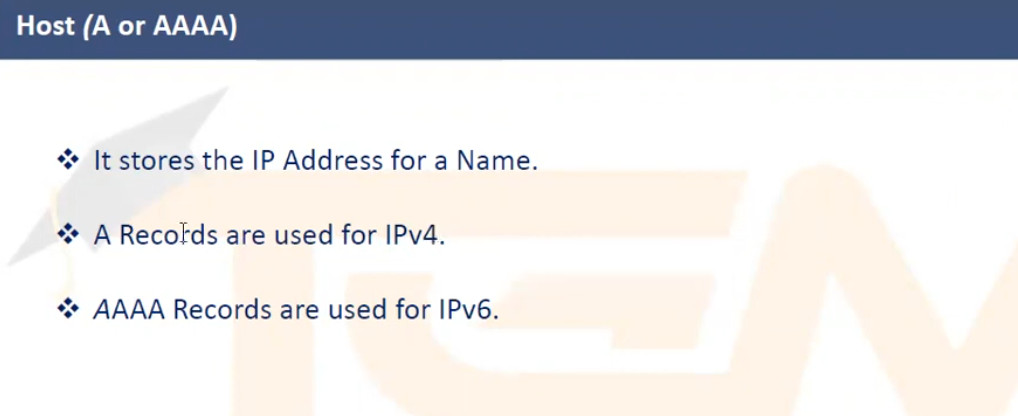
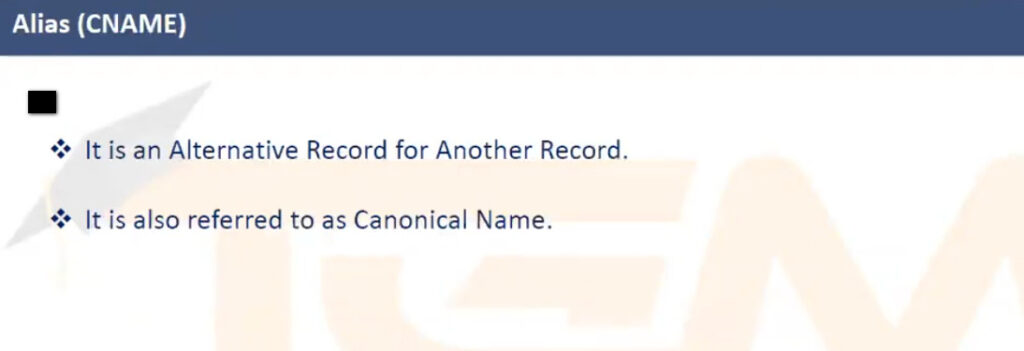
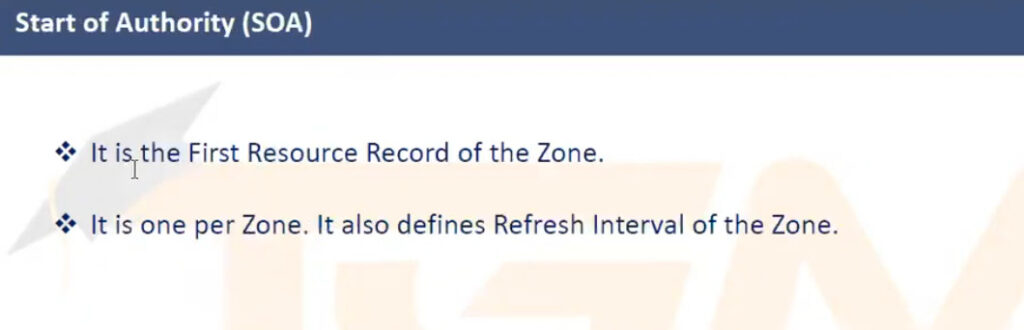
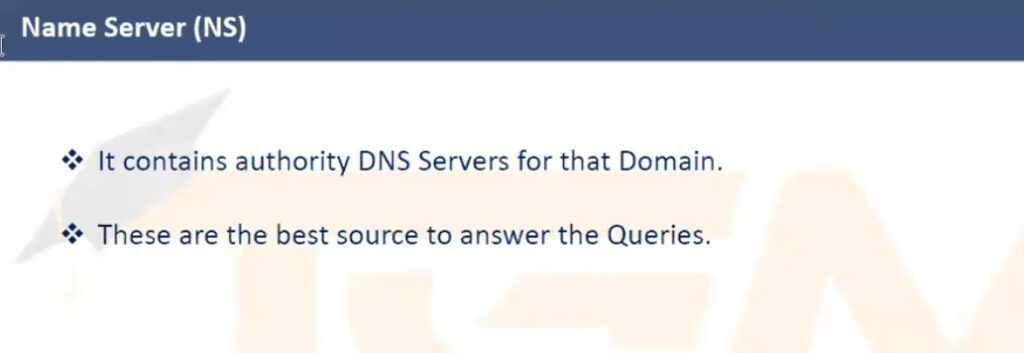
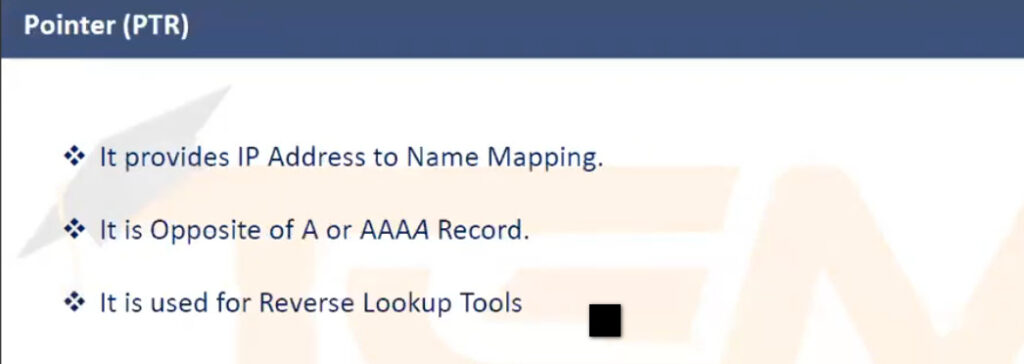
example.com. A 93.184.216.34example.com resolves to the IPv4 address 93.184.216.34.example.com. AAAA 2606:2800:220:1:248:1893:25c8:1946example.com resolves to the specified IPv6 address.www.example.com. CNAME example.com.www.example.com is an alias for example.com.example.com. MX 10 mail.example.com.example.com should be delivered to mail.example.com with a priority of 10 (lower numbers indicate higher priority).example.com. NS ns1.exampledns.com.ns1.exampledns.com is an authoritative nameserver for example.com.34.216.184.93.in-addr.arpa. PTR example.com.93.184.216.34 maps to the domain example.com.example.com. TXT "v=spf1 include:_spf.google.com ~all"example.com._sip._tcp.example.com. SRV 10 60 5060 sipserver.example.com.example.com is located at sipserver.example.com on port 5060 with a priority of 10 and weight of 60.example.com. SOA ns1.exampledns.com. admin.example.com. 2021010101 7200 3600 1209600 86400DNS servers handle the process of resolving domain names to IP addresses and vice versa. The types of DNS servers can be categorized based on their role in the DNS resolution process:
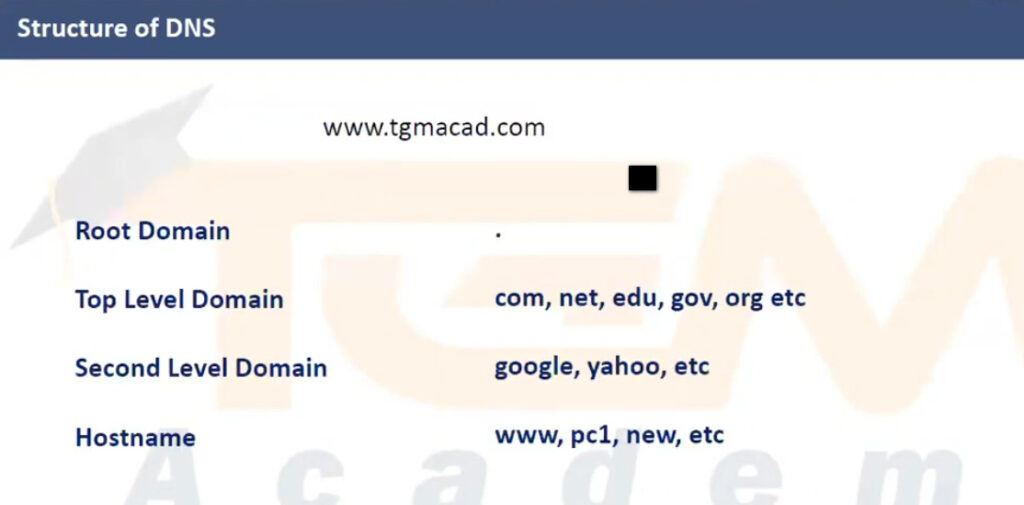
.com, .org, etc.).example.com, the root DNS server will refer the query to the .com TLD server..com, .org, .net). It doesn’t resolve a full domain but points to the authoritative name server for the specific domain..com TLD server would refer example.com queries to the authoritative name server responsible for example.com.example.com will provide the IP address for www.example.com when queried.When a DNS query is made, it can be of several different types, depending on the information requested:
.com TLD server.”93.184.216.34 may return example.com if the PTR record exists for that IP.8.8.8.8 (primary), 8.8.4.4 (secondary)1.1.1.1 (primary), 1.0.0.1 (secondary)208.67.222.222 (primary), 208.67.220.220 (secondary)DNS Check Commands:
| Command | Purpose | Example Usage |
|---|---|---|
nslookup | Query DNS information from a DNS server | nslookup example.com |
dig | Detailed DNS query and troubleshooting | dig example.com MX |
host | Simple DNS query tool for basic lookups | host example.com |
ping | Test DNS resolution and network connectivity | ping example.com |
tracert / traceroute | Trace network route and DNS resolution | tracert example.com |
systemd-resolve | Query DNS information on Linux (systemd) | systemd-resolve example.com |
ipconfig /flushdns | Clear DNS resolver cache (Windows) | ipconfig /flushdns |
resolvectl | Query DNS info on systemd-based Linux systems | resolvectl status |
Mail Record For DNS
In DNS (Domain Name System), email-related DNS records are crucial for ensuring that email systems can route messages to the correct mail servers. The main DNS records related to email are MX (Mail Exchange) records, SPF (Sender Policy Framework) records, DKIM (DomainKeys Identified Mail) records, and DMARC (Domain-based Message Authentication, Reporting & Conformance) records. These records help manage email delivery, prevent spam, and verify the authenticity of sent emails.
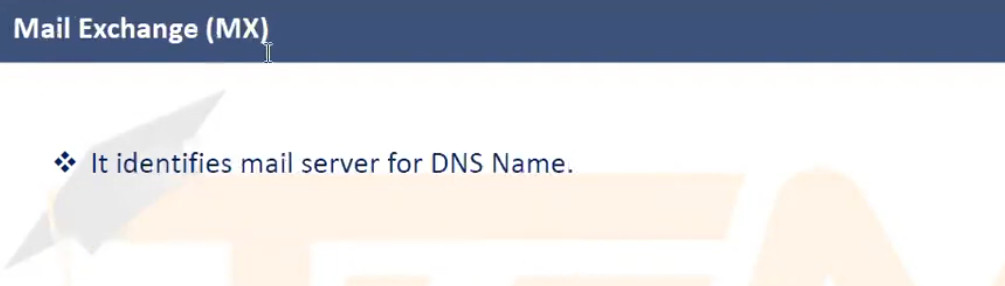
Purpose: The MX record defines the mail servers responsible for receiving email messages for a specific domain. When an email is sent to a domain (e.g., user@example.com), the sending mail server looks up the MX records of example.com to determine where to deliver the message.
Structure: An MX record includes:
mail.example.com).Example:
example.com. MX 20 mail2.example.com.
In this example:
example.com will first be routed to mail.example.com (priority 10).mail.example.com is unavailable, mail will be routed to mail2.example.com (priority 20).Purpose: SPF records are used to prevent email spoofing by specifying which mail servers are authorized to send emails on behalf of a domain. When an email is received, the recipient mail server checks the SPF record of the sending domain to verify that the sender’s IP address is authorized.
Structure: An SPF record is a TXT record that contains a list of authorized sending IP addresses or hostnames.
Example:
This SPF record:
192.168.1.1 to send emails on behalf of example.com.~all means that any other server is “soft-failed,” meaning emails from unauthorized servers should be marked as potentially suspicious but not outright rejected.Purpose: DKIM allows the sender to add a digital signature to their emails, which is then verified by the recipient’s mail server using a public key stored in the DKIM record. It ensures that the email has not been altered during transmission and verifies the authenticity of the sender.
Structure: The DKIM record is a TXT record containing the public key used to verify the digital signature. It also includes other parameters related to the signing algorithm and selector used.
Example:
default._domainkey.example.com. TXT “v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNAD
CBiQKBgQCtLoT1lbklrXYV2Sz0FEkgFf7qHZBQzzbBEnD
1L+JNBxVUsy3FCw9BskdZT3WAtStD
gbTeX5xZnl2Ln4g2+ZTlmF6dCae9phgfUfnP
YQ9zmZUzkrpBQ0PUdxeLDb
mjsfTbw30tYABxH5kLdyEvFpRSsJv94g5VrphbHJALcbA==”
In this example:
default) specifies which key to use from the DKIM records.v=DKIM1 indicates the DKIM version.p= part is the actual public key used to verify the email’s signature.Purpose: DMARC is an email authentication protocol that uses both SPF and DKIM to improve email security and prevent phishing. It allows domain owners to set policies on how to handle emails that fail SPF and/or DKIM checks (such as rejecting, quarantining, or reporting them). DMARC also enables the domain owner to receive feedback on email authentication results.
Structure: The DMARC record is a TXT record that specifies the policy for handling emails and the reporting mechanism.
Example:
_dmarc.example.com. TXT "v=DMARC1; p=reject; rua=mailto:dmarc-reports@example.com; ruf=mailto:dmarc-failures@example.com; sp=none"
In this example:
v=DMARC1: Specifies the DMARC version.p=reject: Emails that fail both SPF and DKIM checks will be rejected.rua=mailto:dmarc-reports@example.com: DMARC aggregate reports will be sent to this email address.ruf=mailto:dmarc-failures@example.com: Forensic reports on failed emails will be sent to this address.sp=none: Policy for subdomains (in this case, no specific policy for subdomains).Purpose: A CNAME record can be used for domain aliases. It’s often used for email-related services when you need to alias a subdomain (e.g., mail.example.com) to a different service or server (e.g., mailservice.provider.com). While not strictly used for email delivery itself, it’s commonly part of the setup for email services.
Example:
mail.example.com is an alias for mailservice.provider.com.| Record Type | Purpose | Example Syntax |
|---|---|---|
| MX | Defines mail servers for the domain. | example.com. MX 10 mail.example.com. |
| SPF | Specifies which mail servers can send email for the domain. | example.com. TXT "v=spf1 ip4:192.168.1.1 ~all" |
| DKIM | Provides a public key for verifying email signatures. | default._domainkey.example.com. TXT "v=DKIM1; k=rsa; p=MIGfMA0G... |
| DMARC | Specifies policy for SPF and DKIM validation and reporting. | _dmarc.example.com. TXT "v=DMARC1; p=reject; rua=mailto:dmarc@... |
| CNAME | Used to alias subdomains for email services (e.g., mail). | mail.example.com. CNAME mailservice.provider.com. |
These records are crucial for email deliverability, security, and reducing spam or phishing attacks. It’s important for domain owners to configure all these records properly to ensure their email system operates securely and reliably.
How Many World DNS Server
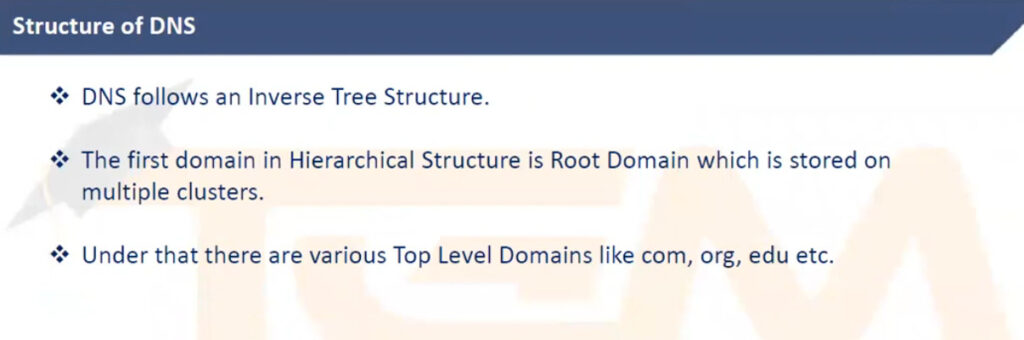
As of 2024, there are 13 root DNS servers in total. These are operated by various organizations and distributed across multiple geographic locations around the world. The root DNS servers are critical to the functioning of the Internet, as they serve as the first step in resolving domain names. They provide the authoritative records for the root zone of the DNS system, essentially directing queries to the appropriate Top-Level Domain (TLD) servers (such as those for .com, .org, .net, etc.).
The root DNS servers are labeled with letters A to M, and they are distributed worldwide using a system called Anycast, which allows multiple copies of the same server to be located in different places. This improves both redundancy and performance by allowing DNS queries to be answered from the nearest available server.
A Root Server
B Root Server
C Root Server
D Root Server
E Root Server
F Root Server
G Root Server
H Root Server
I Root Server
J Root Server
K Root Server
L Root Server
M Root Server
Anycast Technology: Each of the 13 root DNS servers operates using Anycast, meaning that there are actually many instances of each root server spread out across the world in various locations. This helps ensure that DNS queries are handled quickly and reliably, even if some servers experience issues.
Global Distribution: The servers are distributed globally, making them resilient to regional network failures or attacks. For example, root servers are present in North America, Europe, Asia, and other regions to reduce latency and increase reliability.
Critical for DNS Resolution: The root DNS servers are at the top of the DNS hierarchy. When you type a domain name into your browser, your local DNS resolver often needs to query a root DNS server to find the appropriate Top-Level Domain (TLD) server. From there, the query moves downward to authoritative DNS servers that resolve the domain to its IP address.
Security and Stability: These servers are managed by well-established organizations, and their operation is critical to the global Internet infrastructure. They are highly protected and monitored to ensure the stability and security of the DNS system.
Expanding Capacity: The root DNS infrastructure is continuously evolving to handle more traffic as the Internet grows. Newer technologies like DNSSEC (DNS Security Extensions) are being integrated into root server operations to further enhance security.
When you try to visit a website (e.g., www.example.com), the following steps typically occur:
.com, .org, .net).example.com, which responds with the actual IP address.There are 13 root DNS servers worldwide, which are critical components of the DNS infrastructure. They help route queries to the correct top-level domain (TLD) servers, ensuring that domain names can be resolved into IP addresses. These servers are distributed across multiple locations using Anycast technology to improve performance, security, and redundancy.
World Public DNS Server Address
There are several public DNS servers provided by various organizations around the world that offer free, fast, and secure DNS resolution services. These DNS servers can be used as alternatives to the default DNS servers provided by your Internet Service Provider (ISP). Below is a list of popular public DNS server addresses provided by some well-known organizations, along with some details about their services:
Google provides one of the most widely used public DNS services, known for its speed and reliability.
8.8.8.88.8.4.42001:4860:4860::88882001:4860:4860::8844Features:
Cloudflare offers a privacy-focused DNS service that emphasizes security and speed, including support for DNS over HTTPS (DoH) and DNS over TLS (DoT).
1.1.1.11.0.0.12606:4700:4700::11112606:4700:4700::1001Features:
OpenDNS provides DNS services with added security features, such as phishing protection and content filtering.
IPv4 addresses:
208.67.222.222208.67.220.220IPv6 addresses:
2620:119:35::352620:119:53::53Features:
Quad9 is a security-focused DNS service that blocks access to known malicious websites by checking domain names against threat intelligence feeds.
IPv4 addresses:
9.9.9.9149.112.112.112IPv6 addresses:
2620:fe::fe2620:fe::9Features:
Comodo offers a free DNS service with a focus on security, blocking phishing sites, malware domains, and other malicious content.
8.26.56.268.20.247.20Features:
CleanBrowsing offers a family-friendly DNS service, with different filtering levels for content filtering. They focus on providing a safer browsing experience, especially for children.
185.228.168.168185.228.169.169185.228.168.9185.228.169.9185.228.168.88185.228.169.88Features:
DNS.Watch is a German-based DNS provider that offers a privacy-focused, uncensored DNS service with no logging.
84.200.69.8084.200.70.402001:1608:10:25::1c04:4f5b2001:1608:10:25::9249:d69bFeatures:
AdGuard offers DNS services with a focus on blocking advertisements and malicious sites, which can improve privacy and browsing speed.
IPv4 addresses:
94.140.14.1494.140.15.15IPv6 addresses:
2a10:50c0::ad1:ff2a10:50c0::ad2:ffFeatures:
OpenNIC is a user-owned, community-driven project that offers DNS services while emphasizing openness and freedom from censorship.
IPv4 addresses:
169.239.202.202185.121.177.177IPv6 addresses:
2001:470:20::22001:470:20::1Features:
Yandex provides DNS services with features focused on security, performance, and family-friendly filtering.
IPv4 addresses:
77.88.8.877.88.8.1IPv6 addresses:
2a02:6b8::feed:0ff2a02:6b8::feed:0feFeatures:
DNS Advantage is a free public DNS service by a company called Dyn (now part of Oracle). It aims to provide a faster and more reliable DNS service.
IPv4 addresses:
156.154.70.1156.154.71.1IPv6 addresses:
2001:470:20::22001:470:20::3Features:
| Provider | IPv4 Primary DNS | IPv4 Secondary DNS | IPv6 Primary DNS | IPv6 Secondary DNS |
|---|---|---|---|---|
8.8.8.8 | 8.8.4.4 | 2001:4860:4860::8888 | 2001:4860:4860::8844 | |
| Cloudflare | 1.1.1.1 | 1.0.0.1 | 2606:4700:4700::1111 | 2606:4700:4700::1001 |
| OpenDNS | 208.67.222.222 | 208.67.220.220 | 2620:119:35::35 | 2620:119:53::53 |
| Quad9 | 9.9.9.9 | 149.112.112.112 | 2620:fe::fe | 2620:fe::9 |
| Comodo | 8.26.56.26 | `8.20 |