- 8777701917
- info@saikatinfotech.com
- Basirhat W.B










The Palo Alto Networks Certified Network Security Administrator (PCNCA) certification covers various essential topics related to the configuration and management of Palo Alto firewalls. Here’s an overview of the typical syllabus:
1.Introduction to Palo Alto Networks
– Overview of Palo Alto Networks technologies
– Security challenges and solutions
2. Platform Architecture
– Understanding hardware and software architecture
– Control and data planes
3. Initial Configuration
– Setting up a Palo Alto firewall
– Basic configuration steps (management access, interfaces, etc.)
4. Security Policies
– Creating and managing security policies
– Policy rules and best practices
5. Network Address Translation (NAT)
– Configuring NAT rules
– Static and dynamic NAT
6. User Identification
– User-ID technology and configuration
– Integration with Active Directory and other directory services
7. Monitoring and Logging
– Using the web interface for monitoring
– Log management and analysis
8. VPN Configuration
– Setting up site-to-site and remote access VPNs
– Understanding encryption protocols
9. Threat Prevention
– Configuring threat prevention features (IPS, Antivirus, Anti-Spyware)
– Best practices for threat management
10. High Availability
– Implementing HA configurations
– Failover processes and configurations
11. Troubleshooting
– Common troubleshooting techniques
– Diagnostic tools available in Palo Alto firewalls
Next-Generation Security Platform and Architecture
Virtual and Cloud Deployment
Active/Passive High Availability
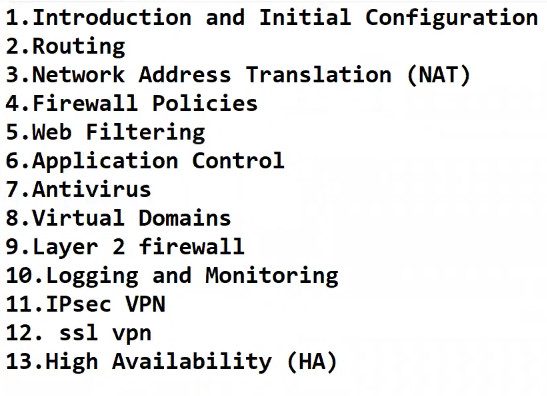
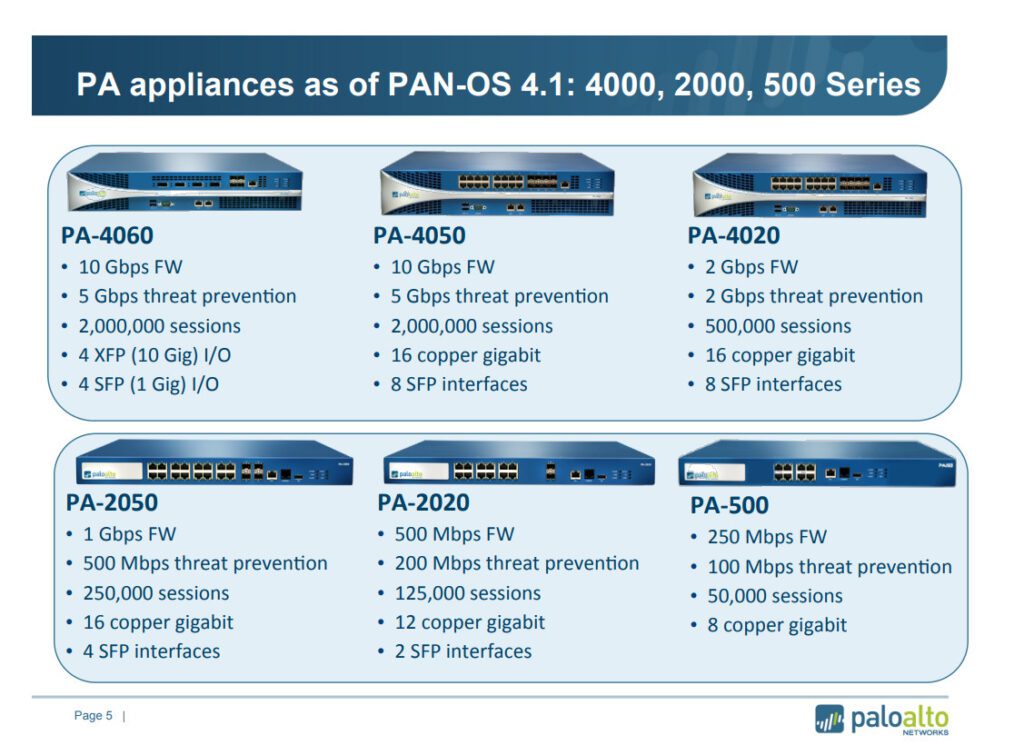
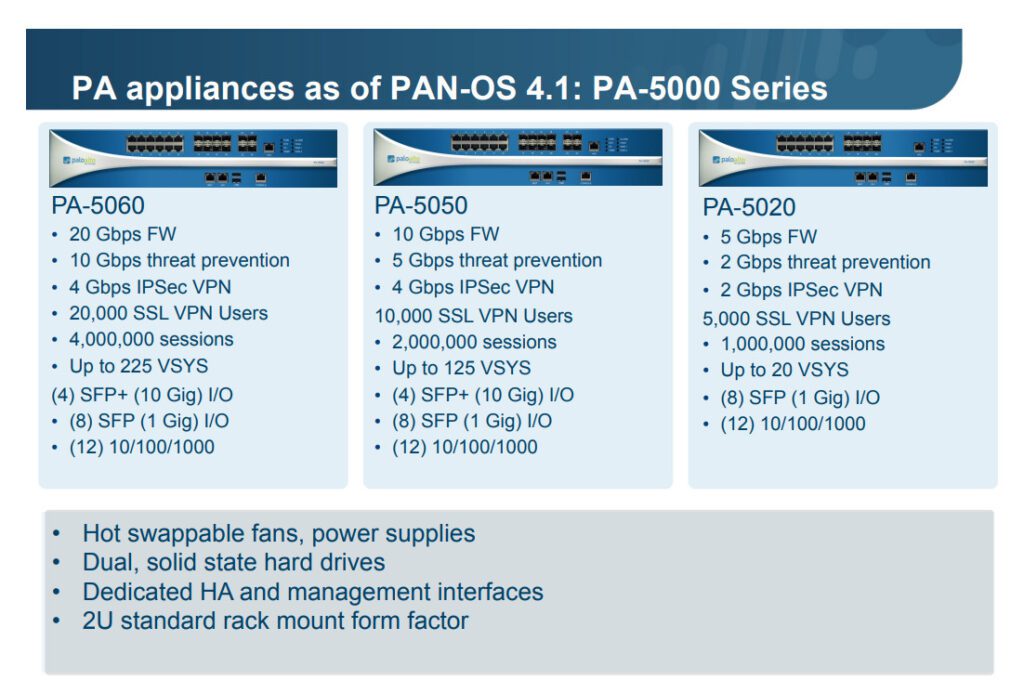
Palo Alto Networks offers a range of firewall models designed for various deployment scenarios, from small businesses to large enterprises. Here’s a list of some common models:
1. PA-Series (Hardware Firewalls)
– PA-220: Ideal for small businesses and branch offices.
– PA-850: Suitable for mid-sized businesses with higher throughput needs.
– PA-3220: Designed for large enterprises and data centers, offering robust performance.
– PA-3250: Enhanced performance and features for larger networks.
– PA-3260: High throughput and advanced features for demanding environments.
– PA-5220: For large data centers and enterprises, with high scalability.
– PA-5260: Advanced model for large-scale deployments with the highest throughput.
– PA-7080: A top-tier model for high-performance, large enterprise, and data center needs.
2. VM-Series (Virtual Firewalls)
– VM-100: For small to medium-sized deployments in virtualized environments.
– VM-300: For mid-sized enterprises with more demanding security needs.
– VM-500: Suitable for larger enterprises and data centers.
– VM-700: High-performance virtual firewall for large-scale environments.
PA-400 Series