- 8777701917
- info@saikatinfotech.com
- Basirhat W.B
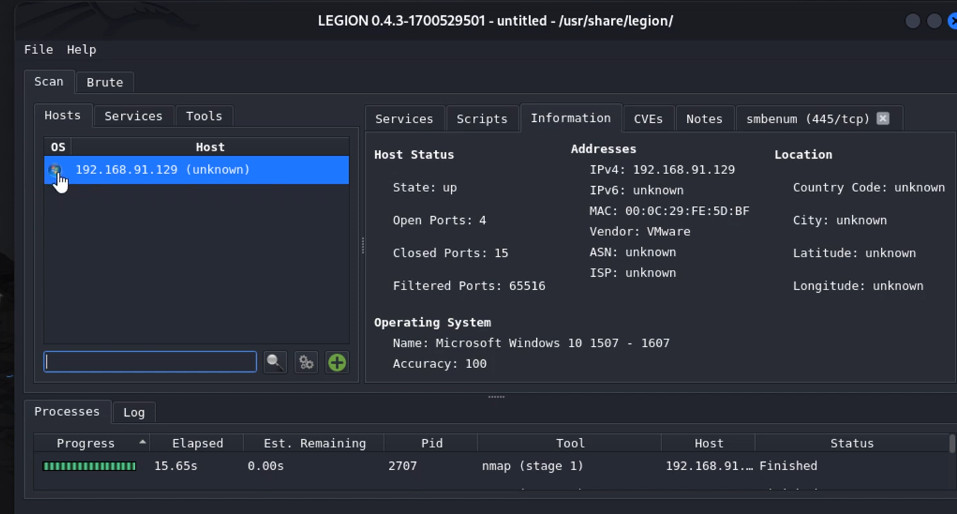
Vulnerability Protection in Palo Alto Networks firewalls is a security feature designed to detect and prevent exploitation of known vulnerabilities in network traffic. It leverages a combination of threat intelligence and intrusion prevention techniques to protect against attacks targeting vulnerabilities in applications, operating systems, and network protocols.
Threat Database:
Signature-Based Protection:
Custom Rules:
Logging and Reporting:
Integration with Other Security Features:
Policy Control:
Create a Vulnerability Protection Profile:
Apply the Profile to a Security Policy:
Monitor Logs: