- 8777701917
- info@saikatinfotech.com
- Basirhat W.B
The FSMO (Flexible Single Master Operation) roles are a set of special roles in a Microsoft Active Directory (AD) environment that are critical for the proper functioning of the AD infrastructure. These roles are responsible for specific operations and ensure that the domain controller (DC) acts efficiently and consistently across the network.
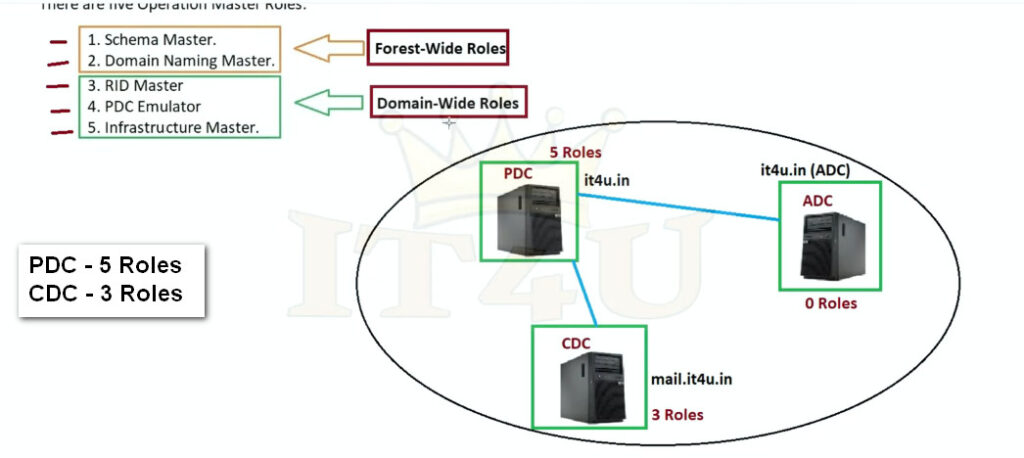
There are five FSMO roles in total, and they are split across three main categories:
What are FSMO roles?
Flexible single-master operator (FSMO) roles are special roles assigned to Active Directory domain controllers (DCs). Each FSMO role can be assigned to only one DC at a time, and that DC is the only one permitted to process a particular type of critical change to Active Directory.
The name comes from two factors: The DC chosen to handle a particular type of update functions as the “single-master operator,” and the role is “flexible” because it can be assigned to any DC.
Note that Microsoft has switched to the term “Operation Master roles,” but “FSMO roles” remains in common use.
Purpose of FSMO roles
Understanding the purpose of Active Directory FSMO roles requires a brief history lesson. Early versions of Windows used a single-master model: One DC — the primary domain controller (PDC) — was responsible for processing all updates in a particular domain. While this model makes conflicts impossible, it has a key drawback: If the PDC is unavailable, it’s impossible to perform vital administrative tasks.
Today, Windows uses a multi-master model: Changes to AD can be processed by any domain controller and are then replicated to the other DCs. While this model eliminates the problem of having a single point of failure, it leads to a different issue: What if two or more DCs
Process conflicting updates?
In most cases, these conflicts are resolved by a simple algorithm: the last writer wins. Any earlier changes are discarded.
However, some changes are too important to be subject to this rule. In those cases, Windows prevents conflicts from occurring in the first place by permitting only one DC — the FSMO role owner — to process certain types of changes.
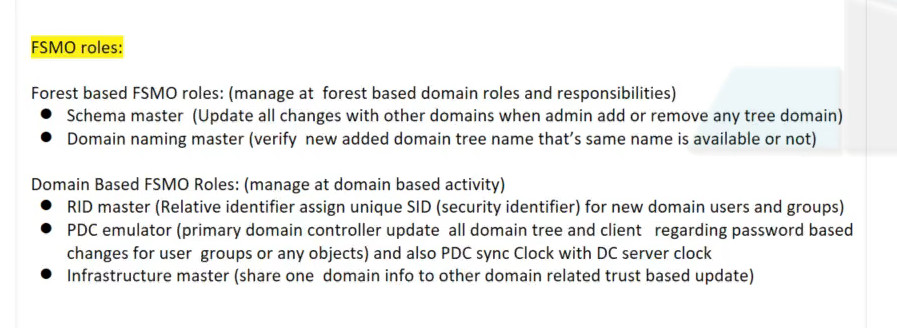
What are the 5 FSMO roles?
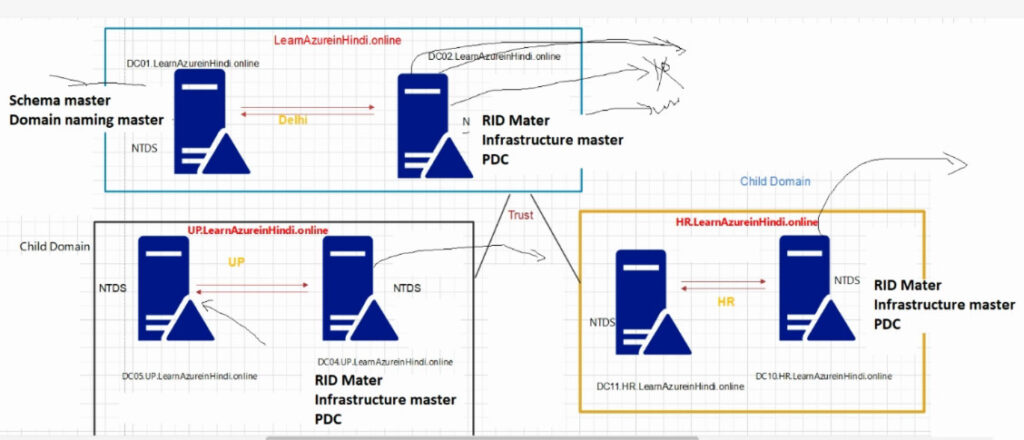
There are five Active Directory FSMO roles:
The same DC can be assigned multiple FSMO roles, or even all five of them. The DC that is assigned a particular FSMO role is called the role owner
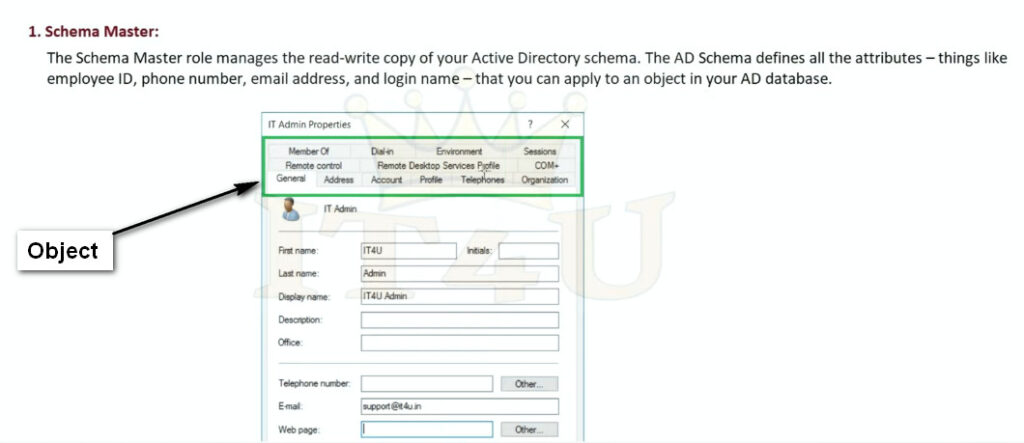
What is the Schema Master role?
In a given forest, only one domain controller has the Schema Master role.
This DC is responsible for processing updates to the directory schema, which are then replicated to all other DCs in the directory. The schema is the blueprint of an Active Directory, with formal definitions of every object class (such as user, computer and security group) that can be created in the AD forest, and every attribute that can exist in an AD object.
For instance, an AD schema might define the following object classes: user, computer, printer and security group. It might allow user objects to have the attributes first name, last name, password, and telephone number, and give printer objects a different set of attributes: model number, location and port.
Examples of actions that update the schema include adding a new custom attribute to an object (such as adding a passport number attribute to user objects), implementing an application that requires an extension of the schema and adding a DC with a new version of Windows Server.
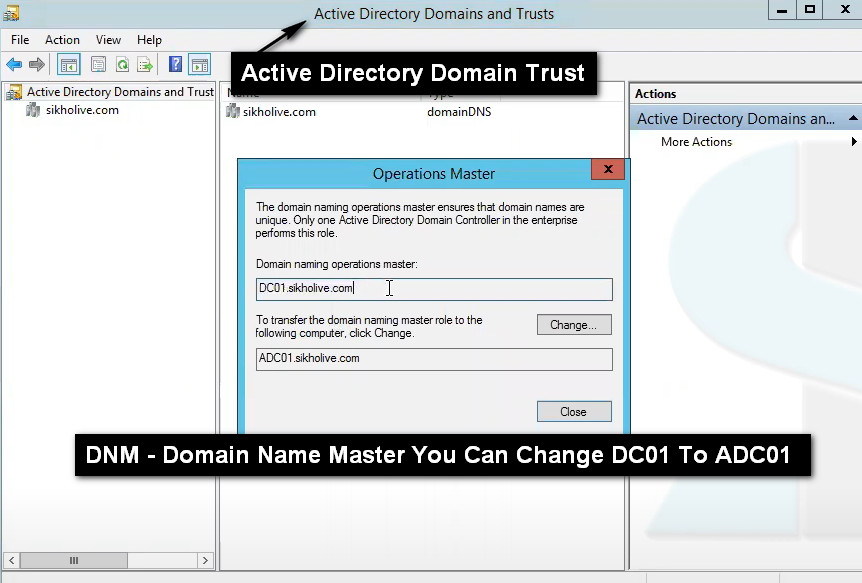
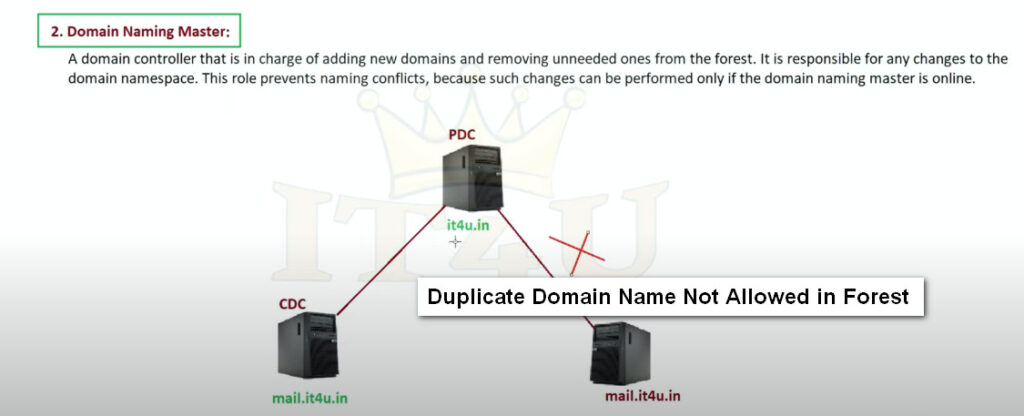
What is the Domain Naming Master role?
In a given forest, only one DC has the Domain Naming Master role.
This DC is responsible for adding and removing domains in the forest. In particular, it ensures that each domain in the forest has a unique name. The Domain Naming Master can also add or remove cross references to domains in external directories.
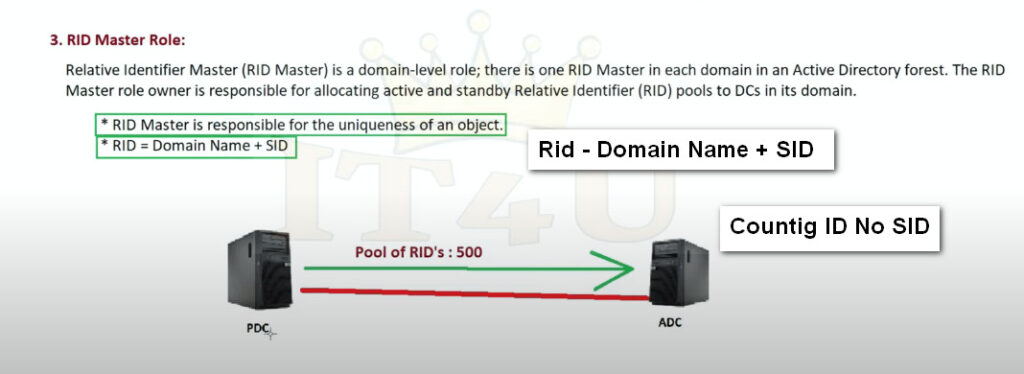
What is the RID Master role?
In each domain, one domain controller is assigned the RID Master role.
This DC is responsible for processing RID pool requests from all DCs in the domain. Each user, group and other security principal is assigned a unique security identifier (SID) when it is created, one component of which is a unique RID. Therefore, each DC needs a pool of RIDs it can assign to the objects it creates. When it runs low, it requests another RID pool from the RID Master.
The RID Master is also responsible for removing an object from its domain and putting it in another domain during an object move.
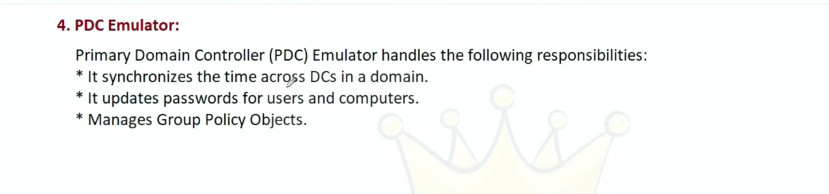
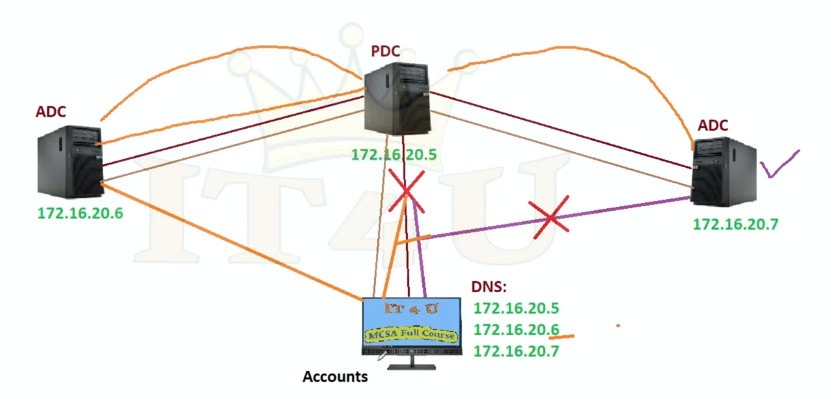
What is the PDC Emulator role?
In each domain, one DC is assigned the PDC Emulator role. This DC is responsible for synchronizing time, which is vital for the integrity of many processes, including Kerberos authentication.
The PDC Emulator of a domain is authoritative for that domain. The PDC Emulator for the domain at the root of the forest is authoritative for the enterprise; it should be configured to collect the time from an external source.
The PDC Emulator is particularly important for password changes and failed authentication events:
Password changes processed by other DCs in the domain are replicated preferentially to the PDC Emulator.
When an authentication attempt fails due to an incorrect password, the failure is sent to the PDC Emulator before the failure message is issued to the user.
Account lockouts are processed on the PDC Emulator.
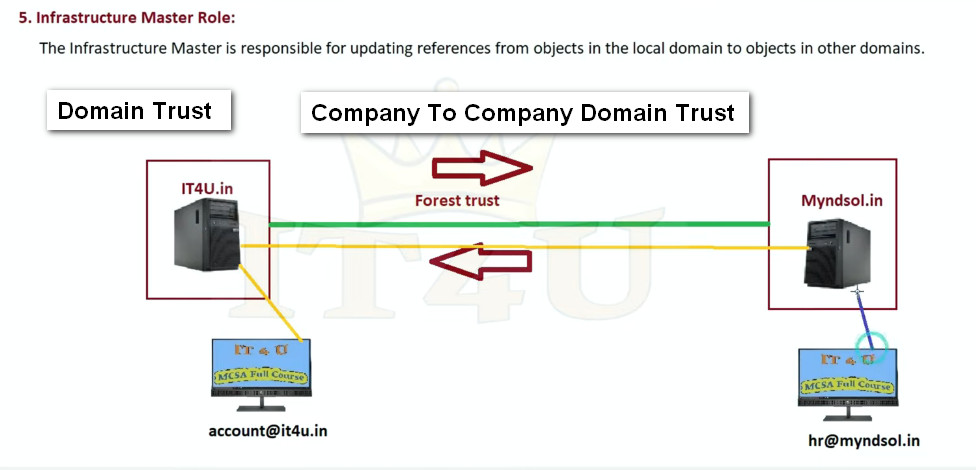
What is the Infrastructure Master role?
In each domain, one DC is assigned the Infrastructure Master role.
This DC is responsible for updating an object’s SID and distinguished name in a cross-domain object reference. In particular, it makes sure that names, rather than cryptic SIDs, appear in your access control lists (ACLs).
This role should be assigned to a DC that is not a Global Catalog (GC) server, unless all the DCs in a domain host the global catalog; in that case, it does not matter which one has the Infrastructure Master role since all the DCs will have current data.
Can an FSMO role be moved from one DC to another?
The DC that owns an FSMO role needs to be available whenever updates it is responsible for need to be made. Some of those updates, such as change to the schema and the addition of new domains, are rare, while other types of changes are more frequent. In particular, the PDC Emulator needs to be accessible at all times.
Administrators can move an Active Directory FSMO role from one DC to another via transfer or seizure:
Transfer — One reason to transfer a role to another DC is that you know that a particular FSMO role owner is going be offline when it will be needed. When the former role holder restarts, it will check inbound replication information, determine that it no longer holds the role and smoothly relinquish role ownership.
Seizure — If a DC that owns an FSMO role crashes and cannot be restored, you can seize the FSMO role and assign it to another domain controller.
For more information about when and how to transfer or seize Active Directory FSMO roles, see the Microsoft guidance.
Primary Main Domain Controler Root DC Use Schema Master
There are two forest wide roles and three domain wide roles
Now let’s take a look at how to query the FSMO roles.
Netdom is a command line tool used to manage Active Directory domains and trusts. The Netdom tool is built into Windows Server 2003 and up.
Step 1. On any domain controller open the command prompt. On Windows server click the start button and type cmd, windows will search and return the command prompt. Click on “Command Prompt”.
Note: You can also run the netdom command using PowerShell.
Step 2. From the command prompt type “netdom query fsmo” and press “enter”.
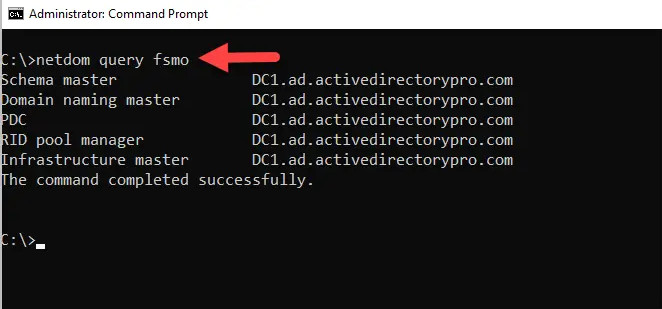
The above command should return the five roles and which DC they are on.
That’s it for the Netdom query method, very simple and straightforward.
Using Powershell will require two lines of code, one to return the forest roles and another to return the domain roles.
Step 1. Open windows PowerShell. On Windows server click start and type Powershell. Click Windows Powershell from the search results
Step 2. Get forest FSMO Roles with the below command.
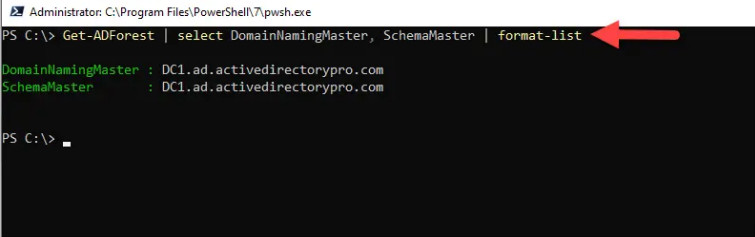
Get-ADForest | select DomainNamingMaster, SchemaMaster | format-list
The above command returns the forest FSMO roles which includes the Schema Master and the Domain naming master.
Step 3. Get domain FSMO roles. with the below command.
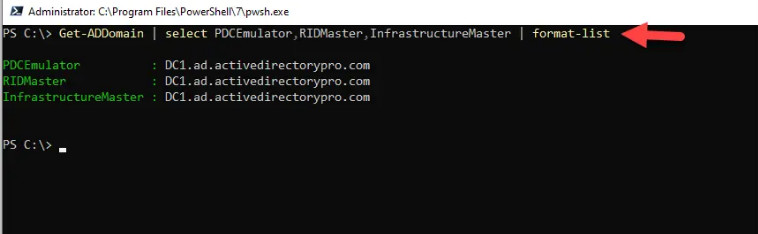
Get-ADDomain | select PDCEmulator,RIDMaster,InfrastructureMaster | format-listThe above command will return the domain FSMO roles PDC, RID pool master and Infrastructure Master).
All 5 roles are initially assigned to the first domain controller (DC) created in a forest. If the forest contains multiple domains, the first DC created in each new domain owns all 3 of the domain-wide FSMO roles for that domain.
However, to ensure fault tolerance, many organizations have multiple domain controllers in each domain of the forest. In this case, they do not need to leave all operations master roles assigned to the original FSMO role holder. In fact, Microsoft recommends that FSMO roles be carefully divided, with standby DCs prepared to take over each role.
Furthermore, Microsoft suggests that the 2 forest-wide roles, Domain Naming Master and Schema Master, should be on the same DC. In a given domain, the PDC Emulator and RID Master roles should be on the same DC.
Below are some other common reasons for transferring FSMO roles to another DC:
It is a best practice to fully document when, where and why FSMO roles are transferred.
To move FSMO roles between DCs, you can use any of the following options:
Each of these options is explained below.
Note that in some cases, you need to seize FSMO roles rather than transfer them. For details, refer to this blog.
To perform FSMO roles transfer, the user account must be a member of the appropriate administrators group, as detailed in the following table:
| To transfer this FSMO role: | A user must be a member of this group: |
| Schema Master | Enterprise Admins |
| Domain Naming Master | Enterprise Admins |
| RID Master | Domain Admins |
| PDC Emulator | Domain Admins |
| Infrastructure Master | Domain Admins |
The Microsoft GUI you use to view and migrate FSMO roles depends on the role involved:
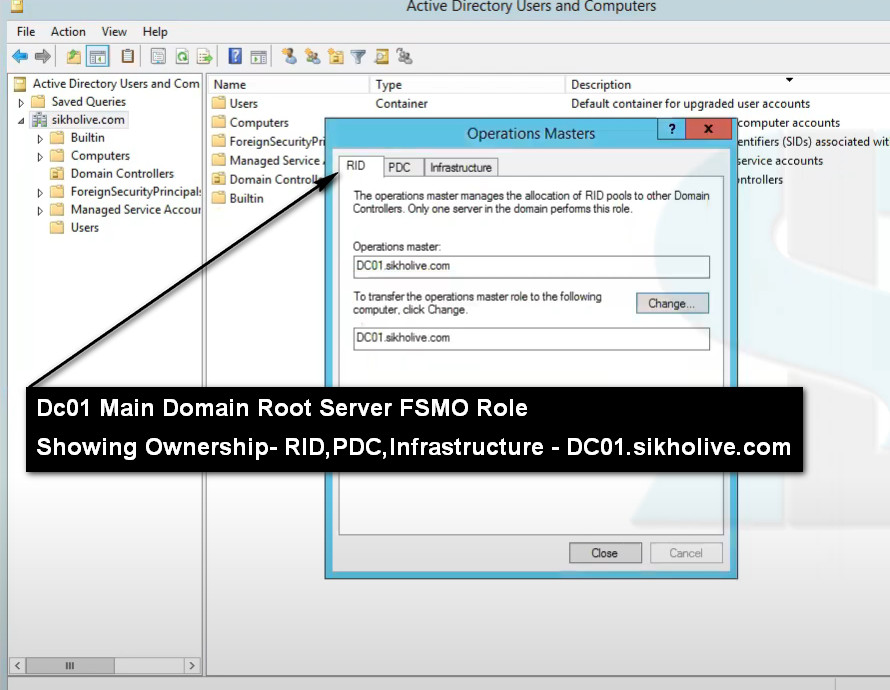
Using ADUC, you can see which domain controller currently holds the RID Master, Infrastructure Master or PDC Emulator role and transfer the role to a different DC. Take the following steps:
1. Using an account that is a member of Domain Admins, log on to the domain controller to which you want to transfer the role.
2. Open ADUC.
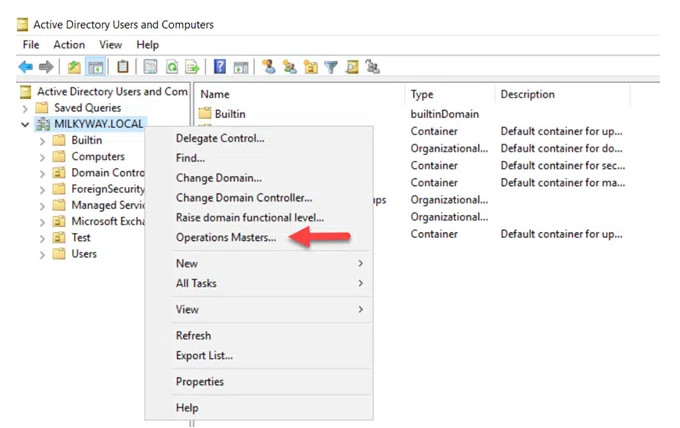
3. Right-click on the domain node and click Operations Masters, as shown below.
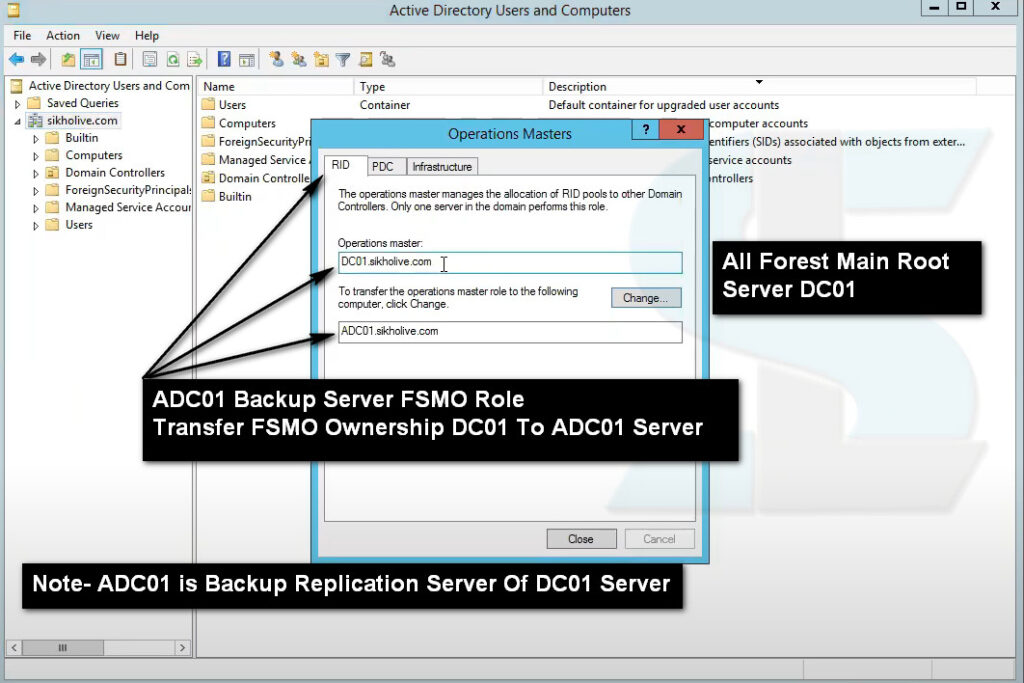
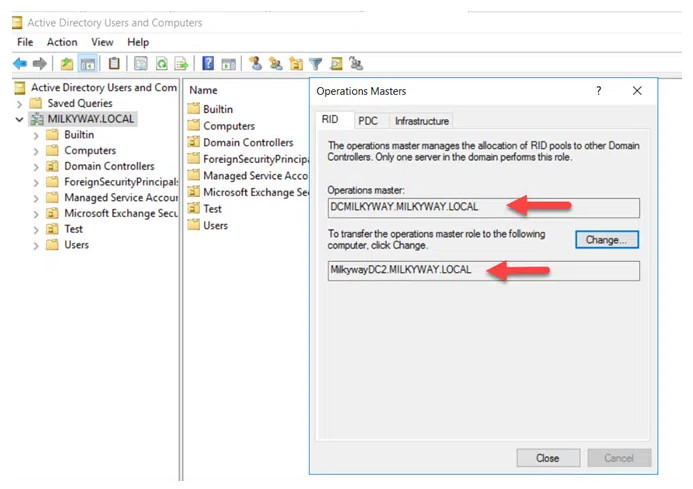
4. In the Operations Masters window, on the RID tab, you can see which domain controller currently holds the RID Master role, as well as the DC that you are logged on to. If you want to change the DC that holds the PDC Emulator or Infrastructure Master role, click the appropriate tab.
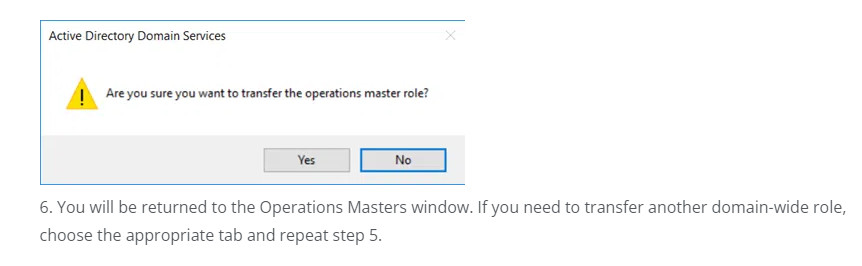
5. To proceed with the role transfer, click the Change button. Then click Yes to confirm the action, as shown below.
You can use ADDT to see which DC holds the Domain Naming Master role and transfer the role to a different DC. Follow the steps below.
1. Using an account that is a member of the Enterprise Admin group, log on to the DC to which you want to transfer the role.
2. Open ADDT.
3. Right-click on the Active Directory Domains and Trusts node and choose Operations Masters.
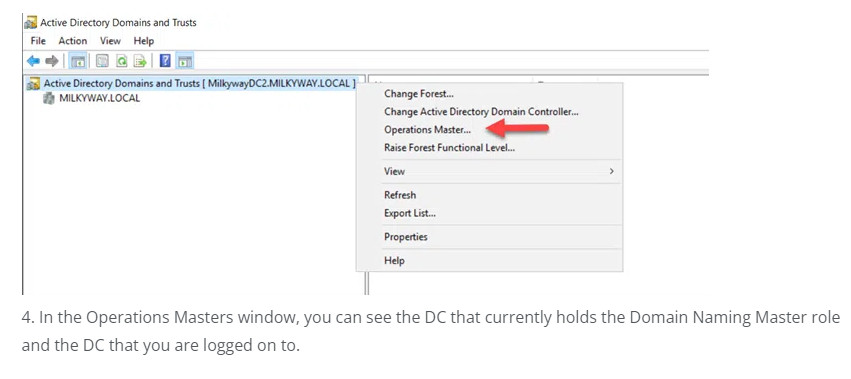

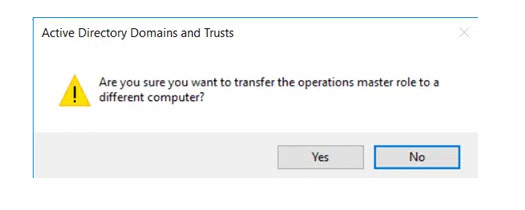
5. To transfer the role from the current DC to the target DC, click the Change button. When asked to confirm the action, click Yes.
Before you can transfer the Schema Master role, you must add the Active Directory (AD) snap-in to MMC console and first register it in the OS.
Note that the exact options vary depending on the version of Windows Server that you are using. The example shows the process for Windows Server 2016.
1. To open the command prompt window, do one of the following:
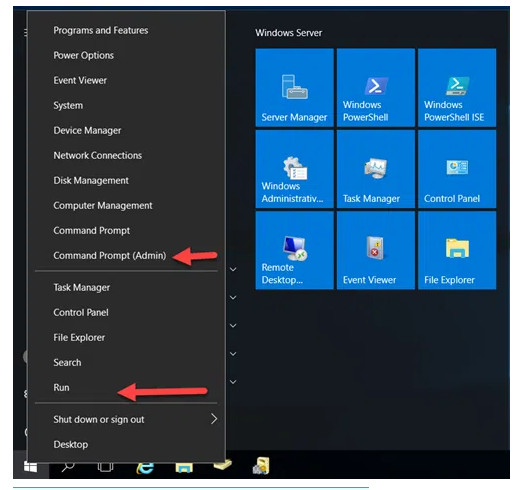
2. Type regsvr32 schmmgmt.dll and press Enter. You will receive a confirmation message that the command succeeded.

3. Open MMC by typing mmc.exe in the Run dialog box.
4. Next, we need to add the Active Directory Schema snap-in. Click File and then choose Add/Remove Snap-In.
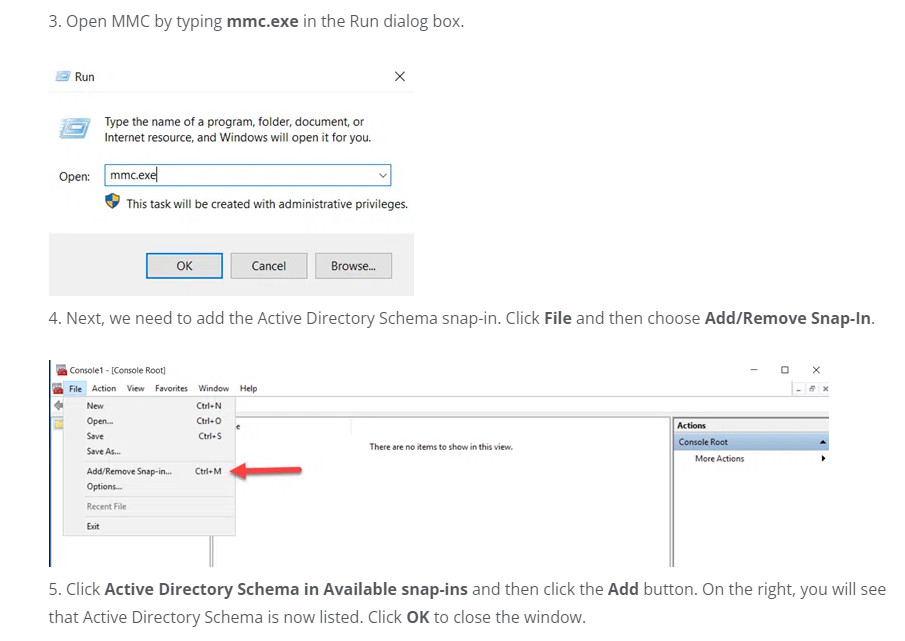
5. Click Active Directory Schema in Available snap-ins and then click the Add button. On the right, you will see that Active Directory Schema is now listed. Click OK to close the window.
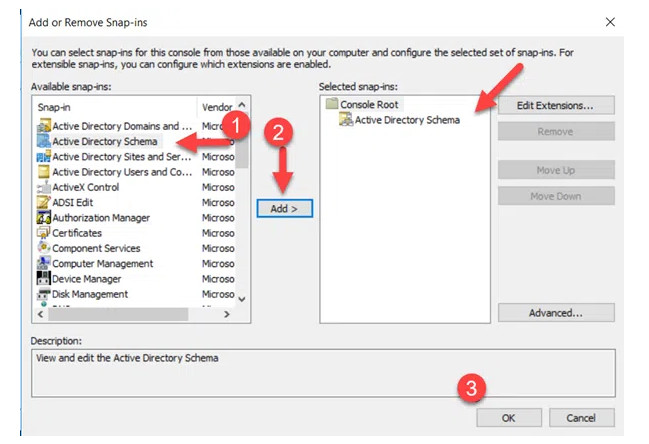
6. The Active Directory Schema snap-in is not connected to the DC that currently holds the Schema Master role — but that isn’t the DC we want to transfer the role to.
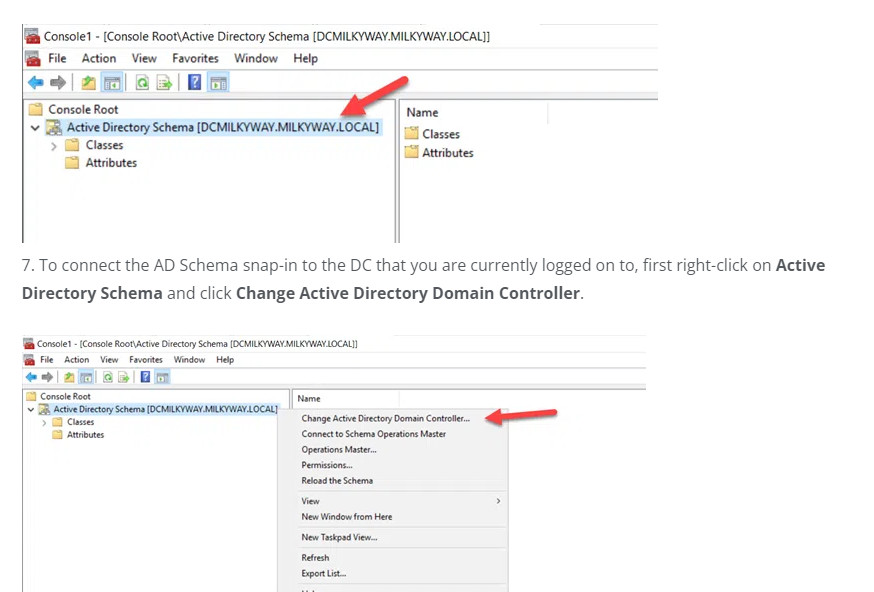
8. Select the This Domain Controller or AD LDS instance radio button and choose the correct DC. Click OK to close the window.

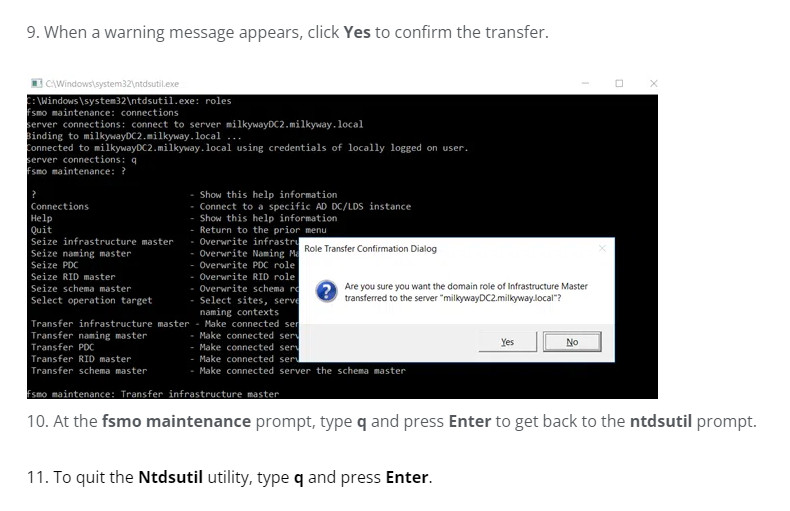
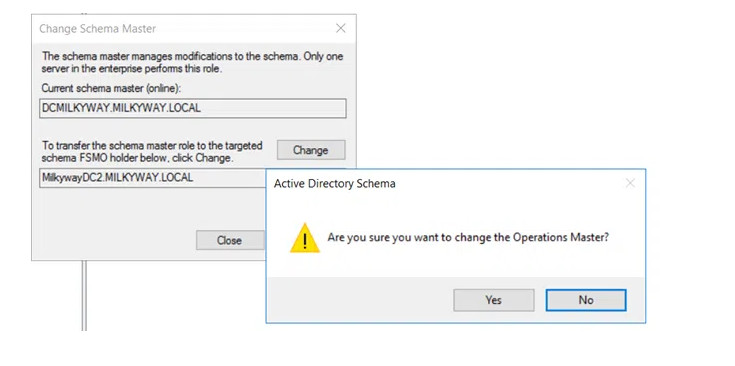
9. When the following warning message appears, click OK.
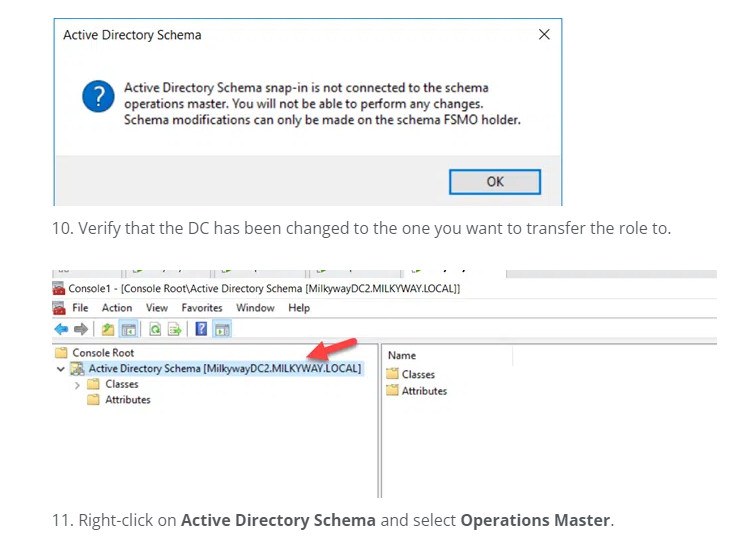
11. Right-click on Active Directory Schema and select Operations Master.
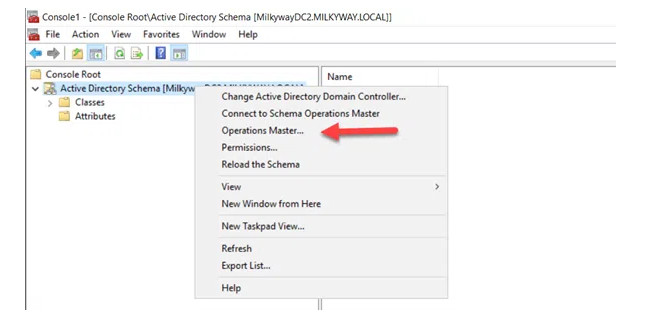
12. You will see the DC that currently holds the Schema Master role and, below it, the DC you are logged on to. To initiate the role transfer, click Change.
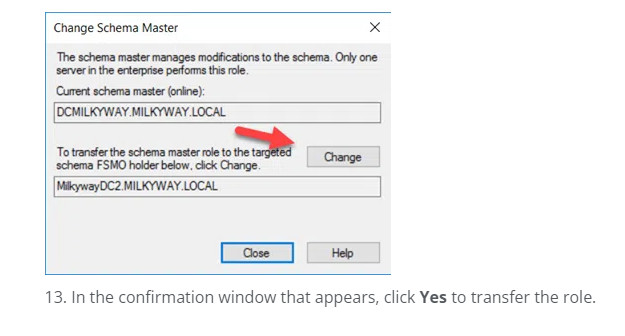
13. In the confirmation window that appears, click Yes to transfer the role.
A third way to transfer FSMO roles is to use the command-line program ntdsutil.exe. Note that only experienced administrators should use this powerful tool.
Here are the steps to take:
1. Log in to either a member computer where AD RSAT tools are installed or a DC located in the same forest where the Operation Master roles exist. It is recommended that you log on to the DC to which you are transferring Operation Master roles.
2. Click Start and type Run. In the Run dialog box, type ntdsutil and click OK.
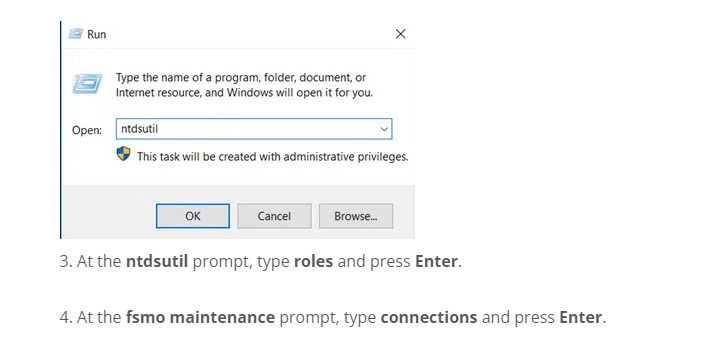
3. At the ntdsutil prompt, type roles and press Enter.
4. At the fsmo maintenance prompt, type connections and press Enter
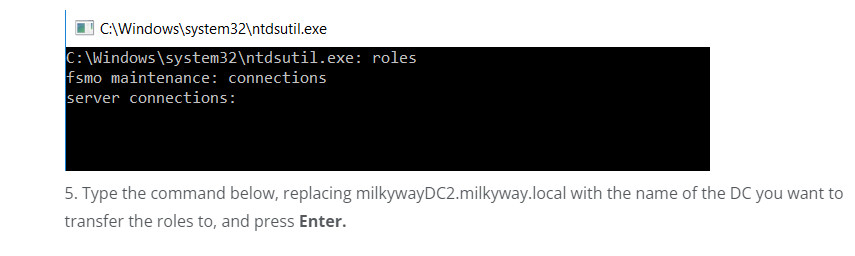
5. Type the command below, replacing milkywayDC2.milkyway.local with the name of the DC you want to transfer the roles to, and press Enter.
connect to server milkywayDC2.milkyway.local 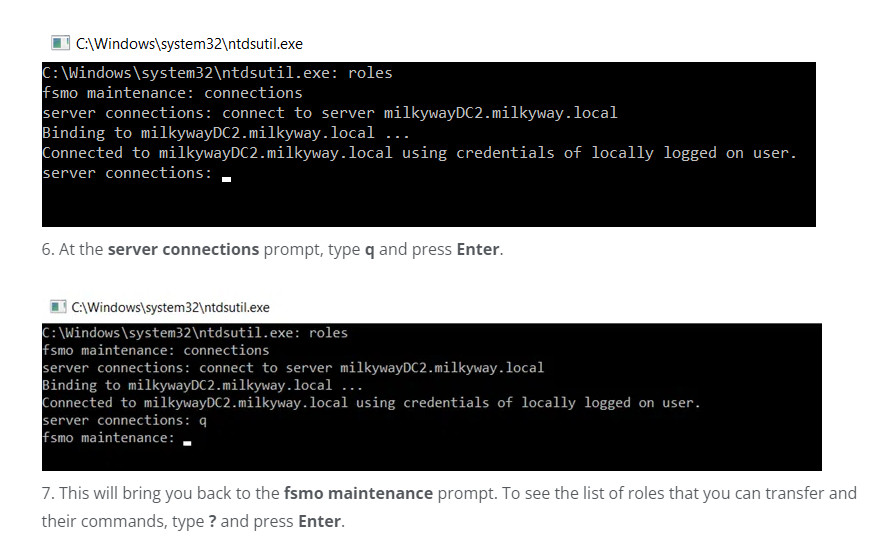
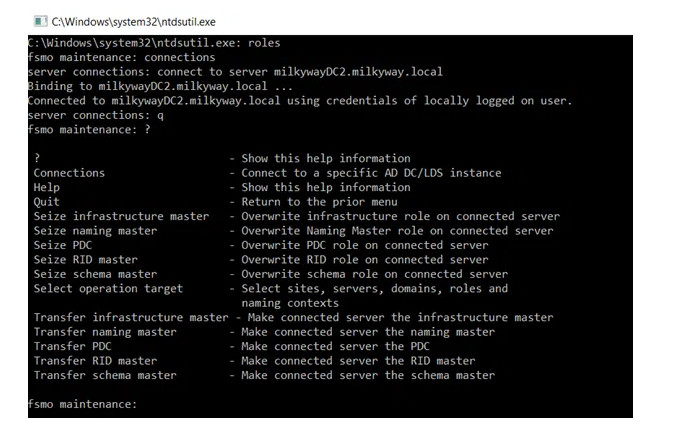
8. To transfer a role, type the corresponding command from the list below and press Enter.
Transfer domain naming master
Transfer infrastructure master
Transfer PDC
Transfer RID master
Transfer schema master