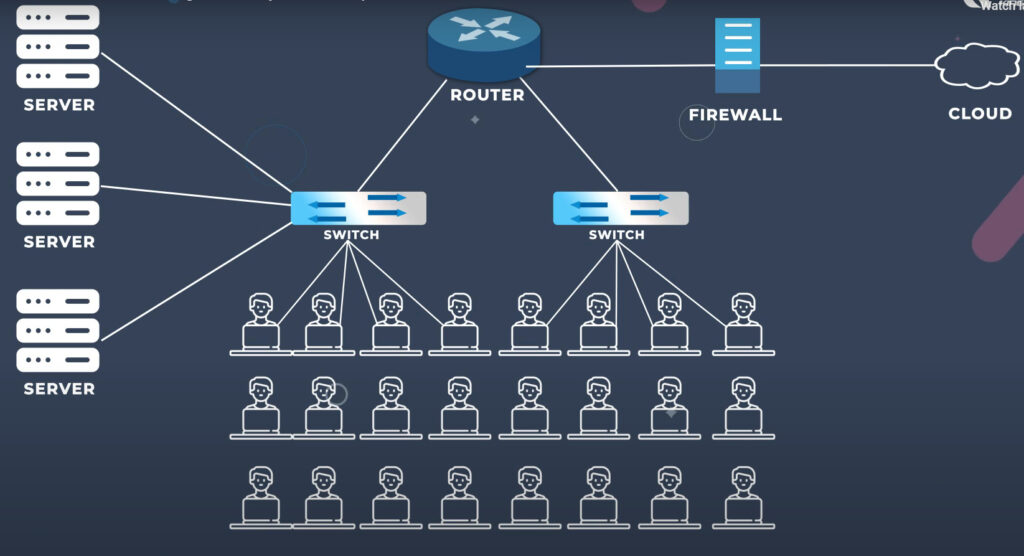
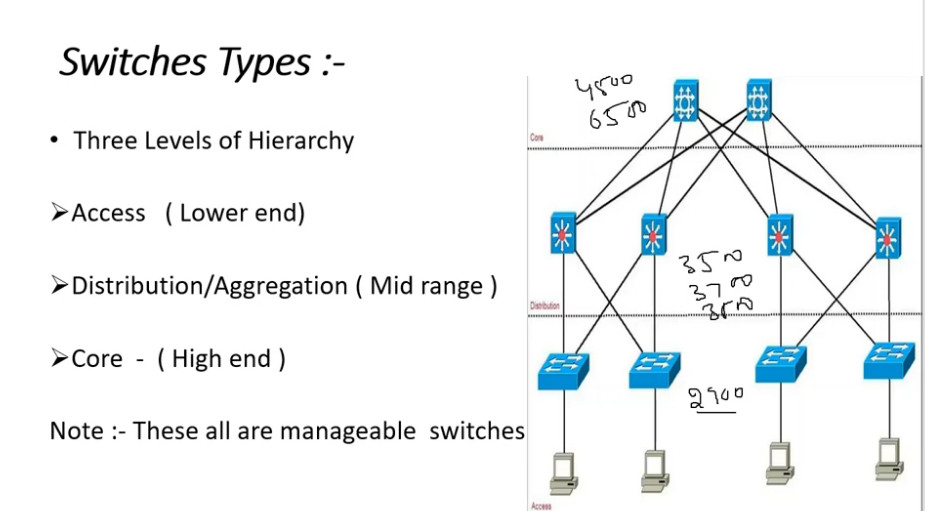
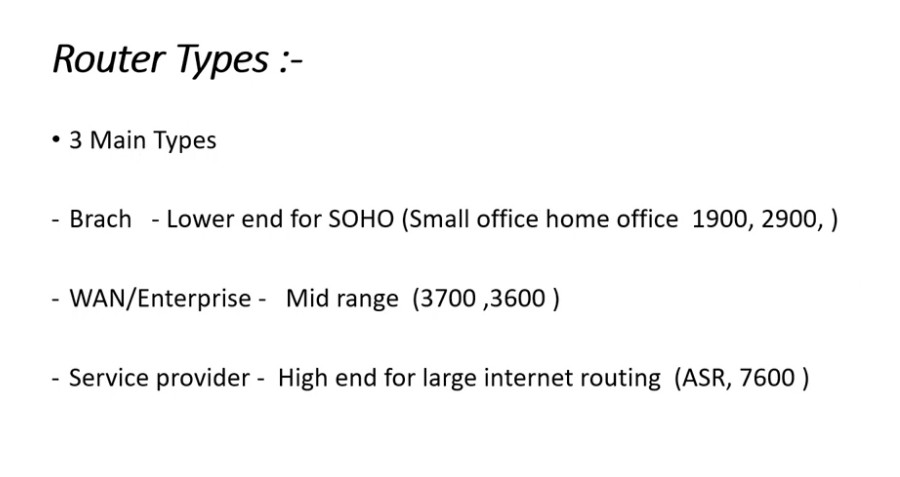
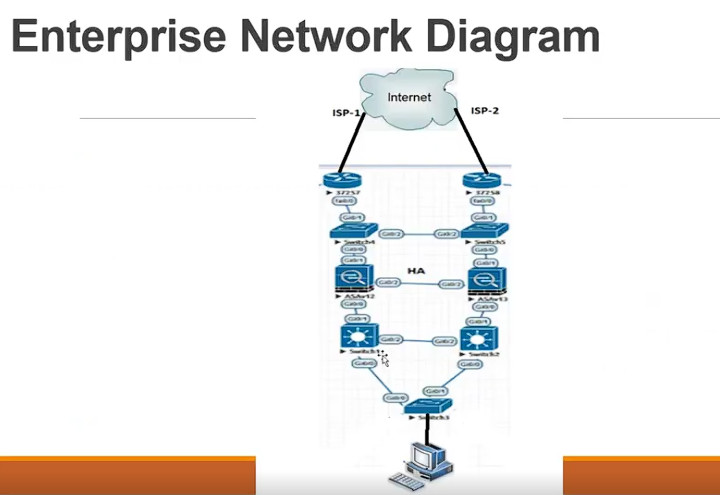
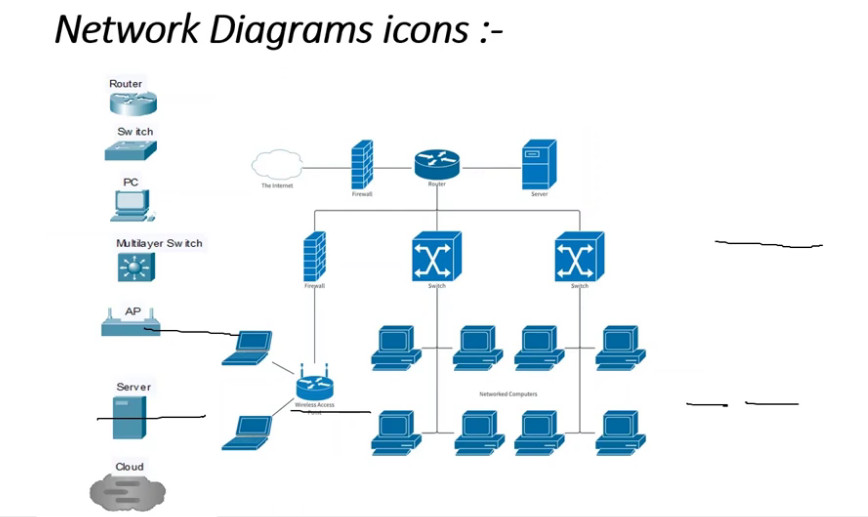
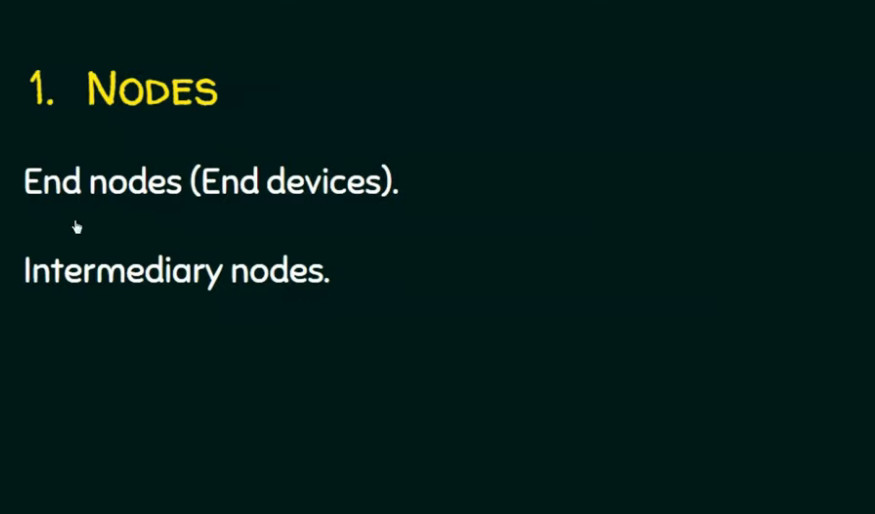
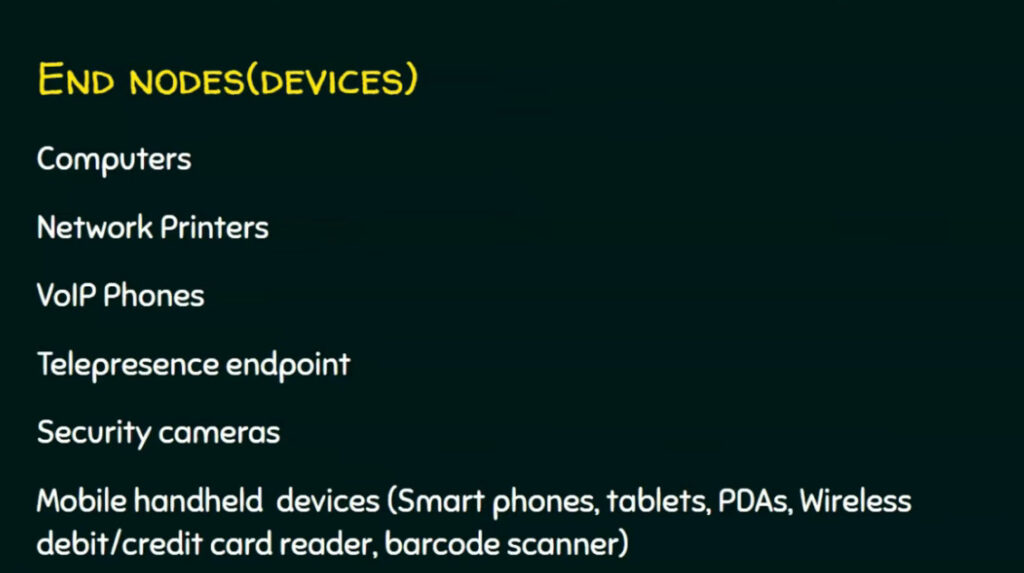
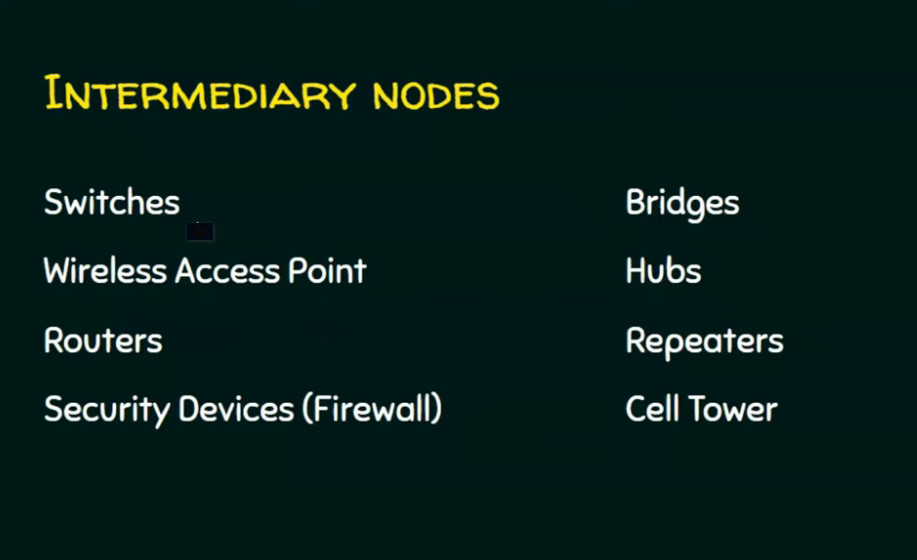
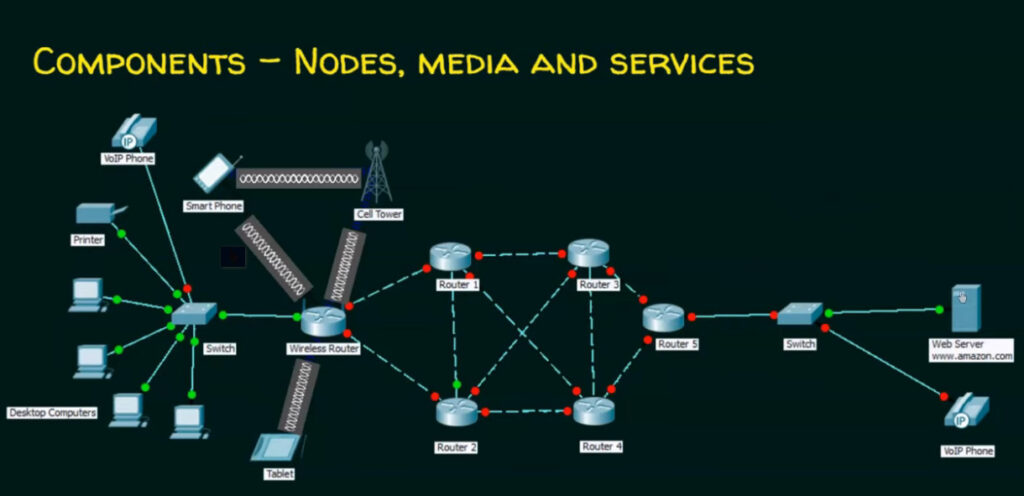
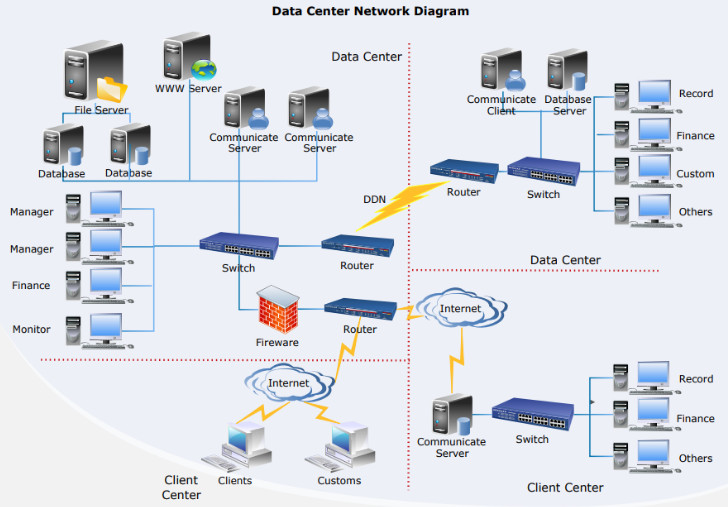
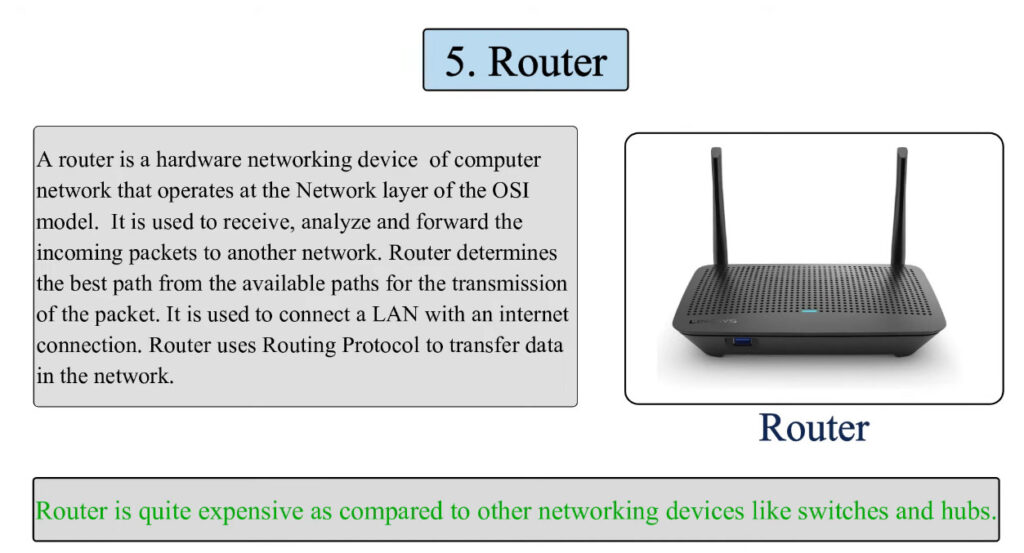
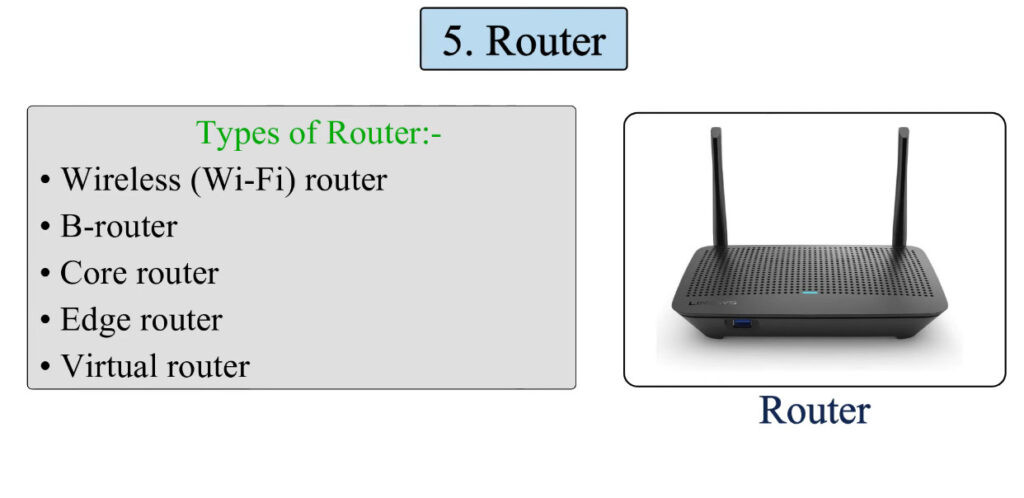
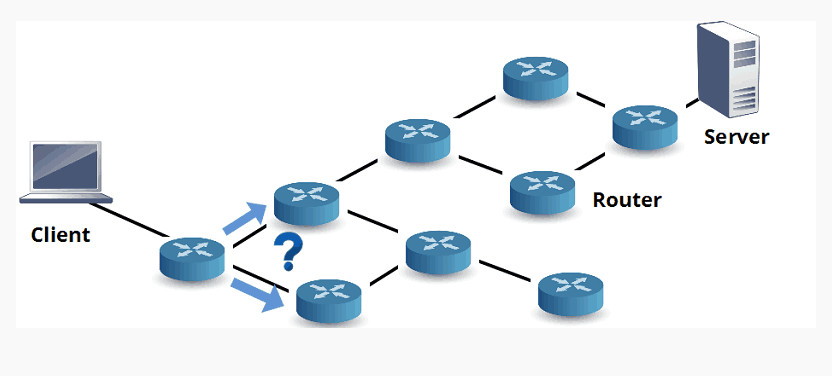
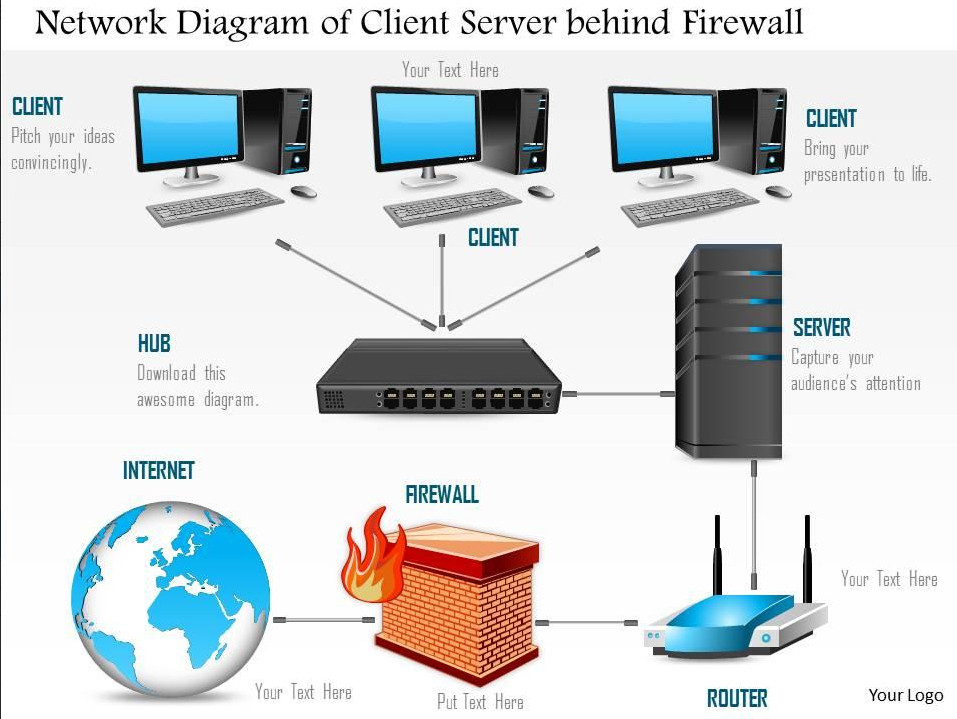
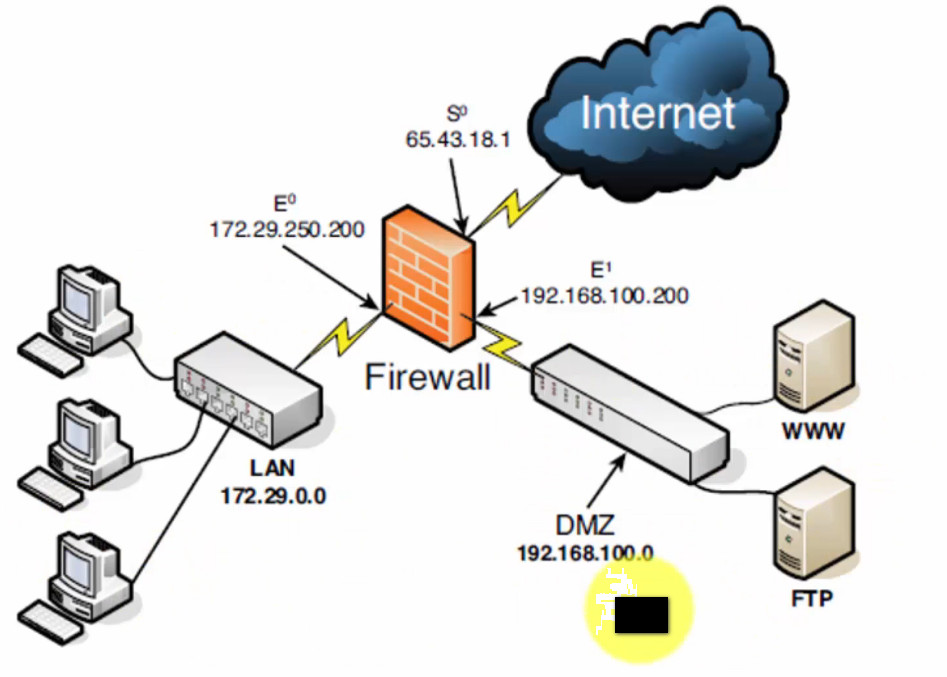
A computer network consists of various components that work together to allow devices to communicate, share resources, and exchange data. Below are the key components of a computer network:
1. Devices (Nodes)
These are the endpoints or devices connected to the network that can send or receive data. Common network devices include:
- Computers: Desktops, laptops, and servers that request or provide services and resources.
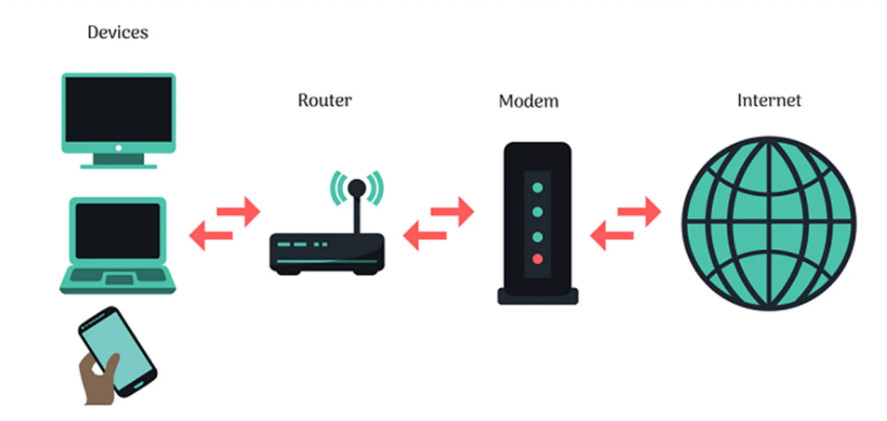
- Routers: Devices that forward data packets between different networks. They determine the best path for data to travel across a network or between networks.
- Switches: Devices that connect devices within a local area network (LAN) and facilitate communication by forwarding data to the correct device.
- Access Points (APs): In wireless networks, access points allow devices to connect wirelessly to the network.
- Printers, Scanners, and Other Peripherals: Shared devices that can be accessed by multiple users on the network.
- Modems: Devices that convert digital data from a computer into analog signals for transmission over telephone lines or vice versa, typically used to connect to the internet.
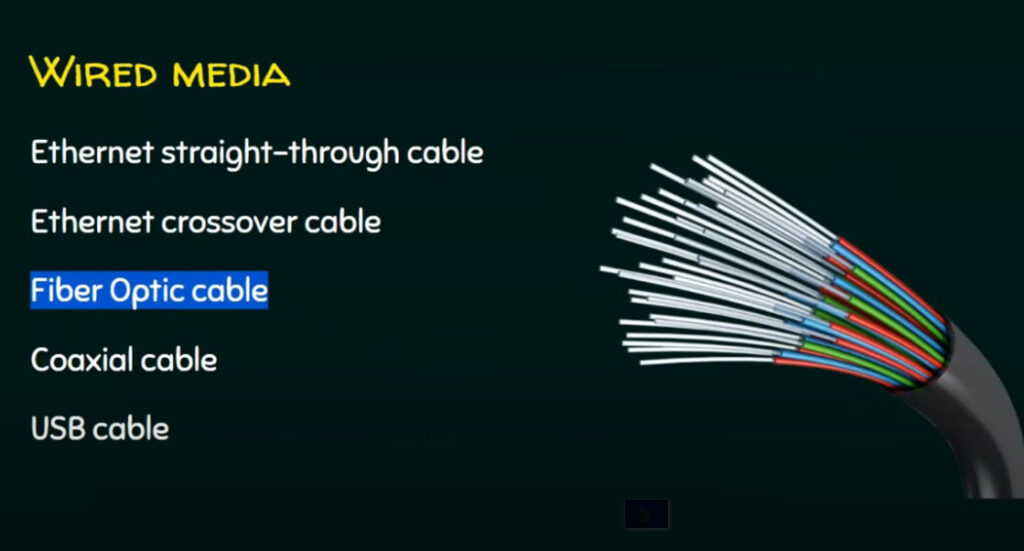
2. Transmission Media
Transmission media refers to the physical or wireless pathways that carry data between devices. The main types include:
- Wired Media:
- Ethernet Cables (Twisted Pair, Fiber Optic, Coaxial): These cables carry data signals between devices. Fiber optics offer high-speed, long-distance transmission.
- Wireless Media:
- Wi-Fi: Wireless communication used to connect devices to the network without cables.
- Bluetooth: Short-range wireless technology for connecting devices in close proximity.
- Satellite and Microwave: Used for long-distance communication.
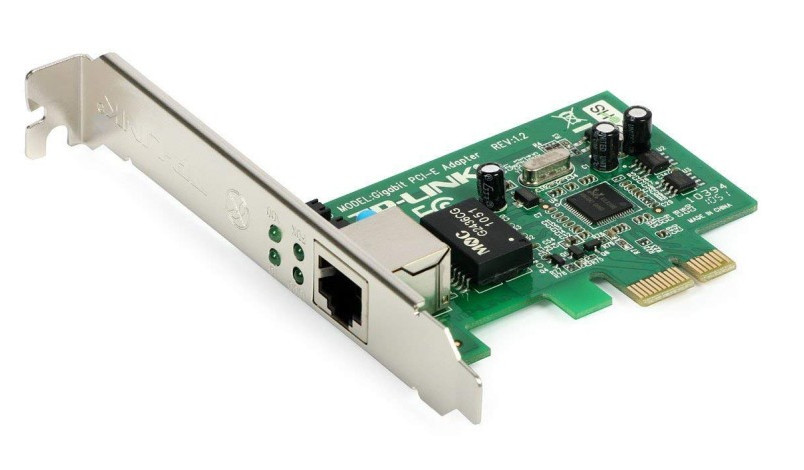
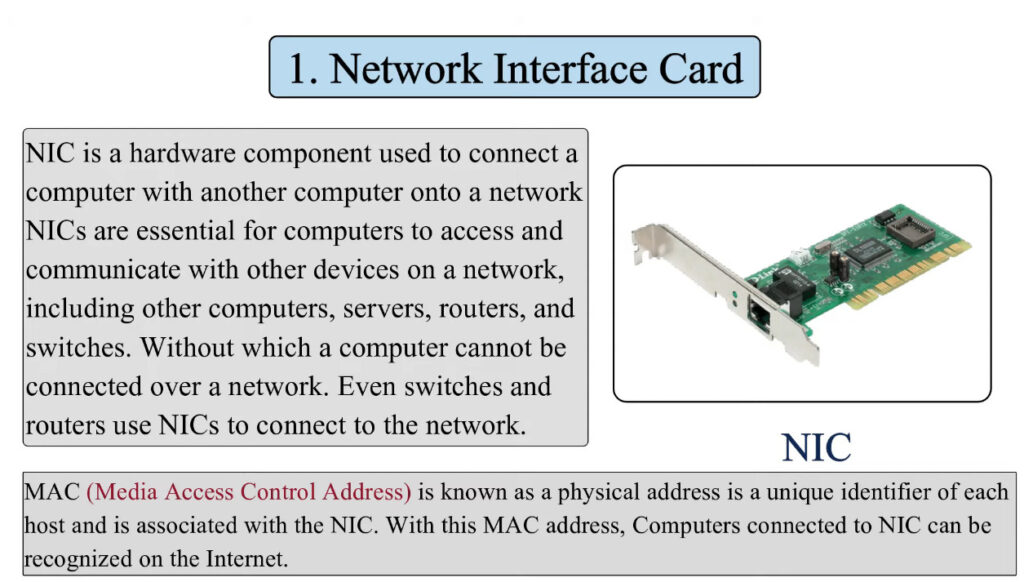
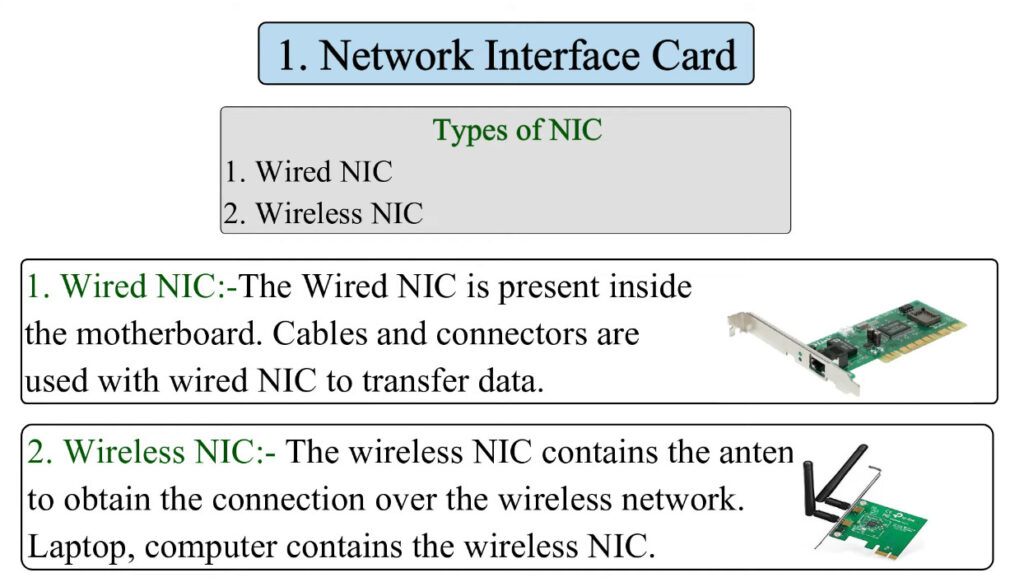
3. Network Interface Cards (NICs)
- NIC is a hardware component (usually a card or built-in chip) that allows devices (computers, printers, etc.) to connect to the network.
- NICs can be wired (Ethernet) or wireless (Wi-Fi) and provide the physical connection to the network.
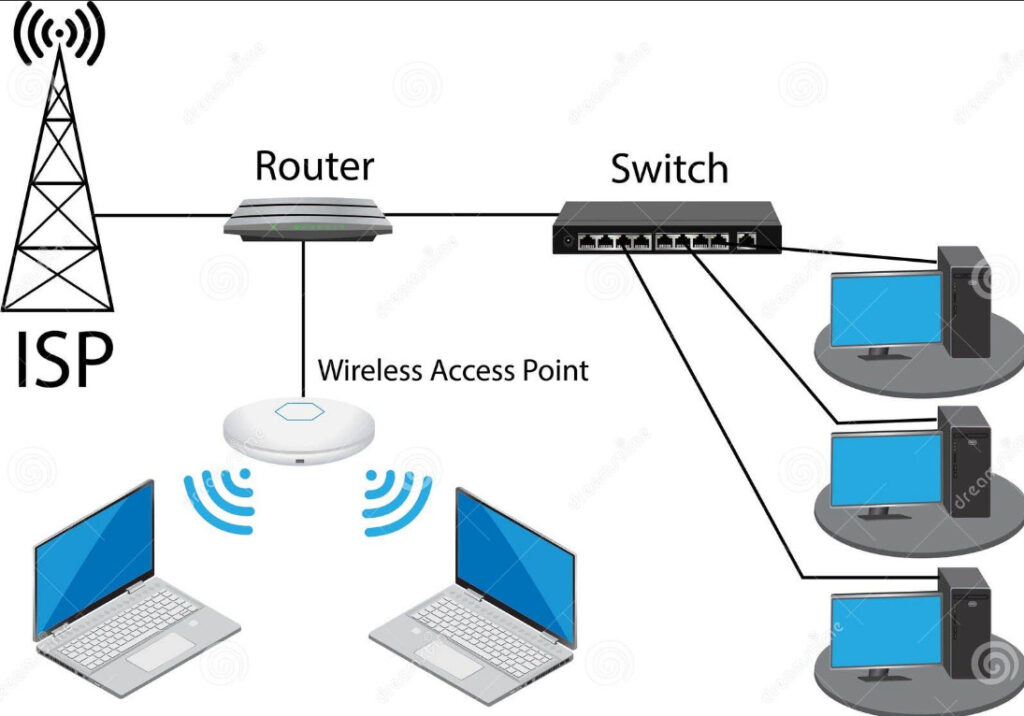
4. Router
- A router connects different networks, such as a local network (LAN) and the internet (WAN).
- It directs data packets from one network to another and ensures that the data reaches the correct destination.
- Routers use IP addresses to forward data efficiently across networks.
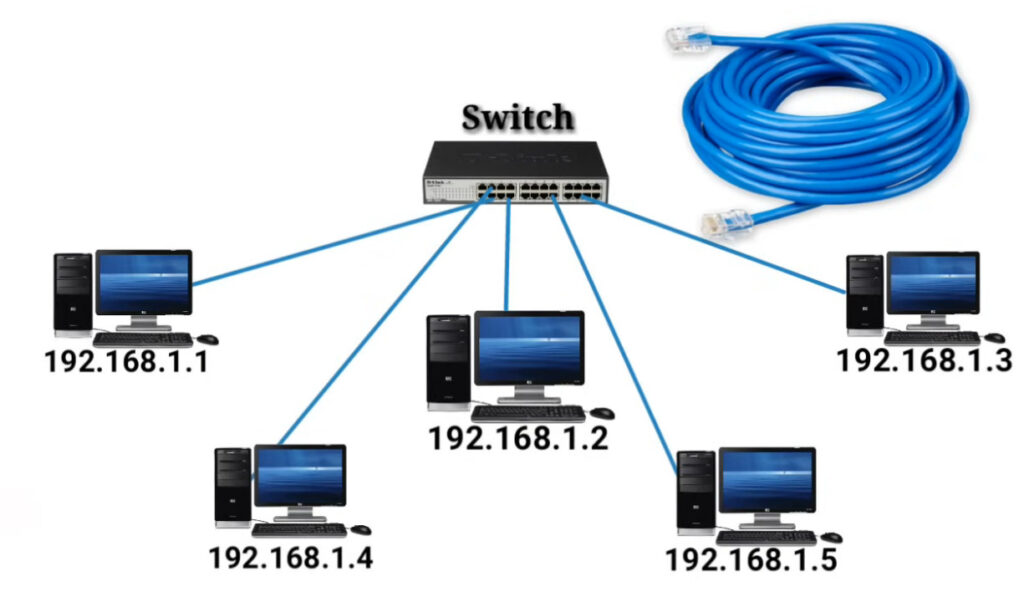
5. Switch
- A switch operates within a LAN and is used to connect multiple devices (computers, printers, etc.) in a network.
- Unlike hubs, switches only send data to the specific device it is intended for, improving network efficiency.
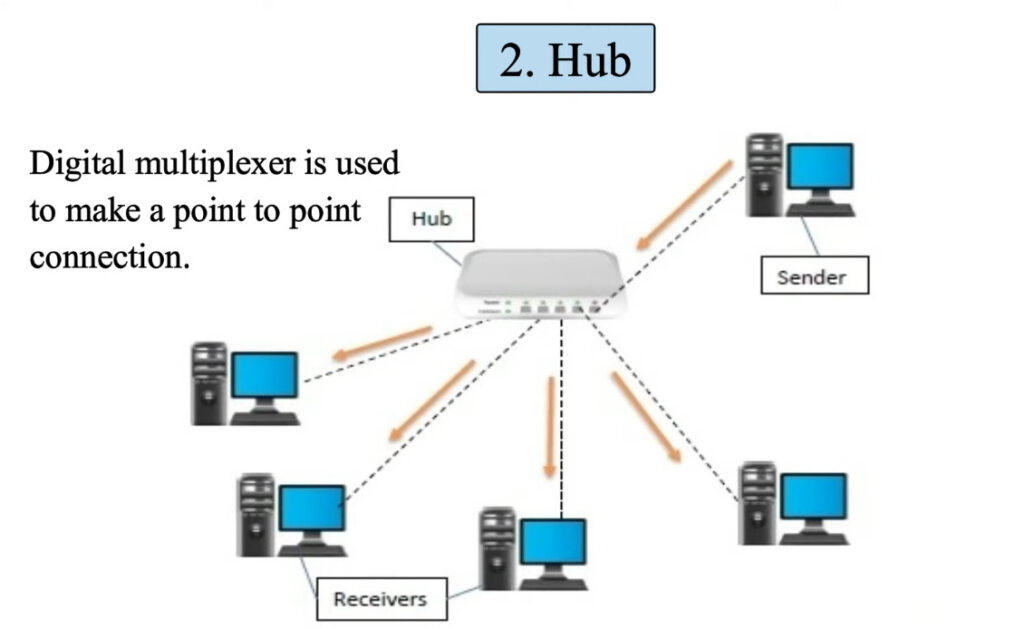
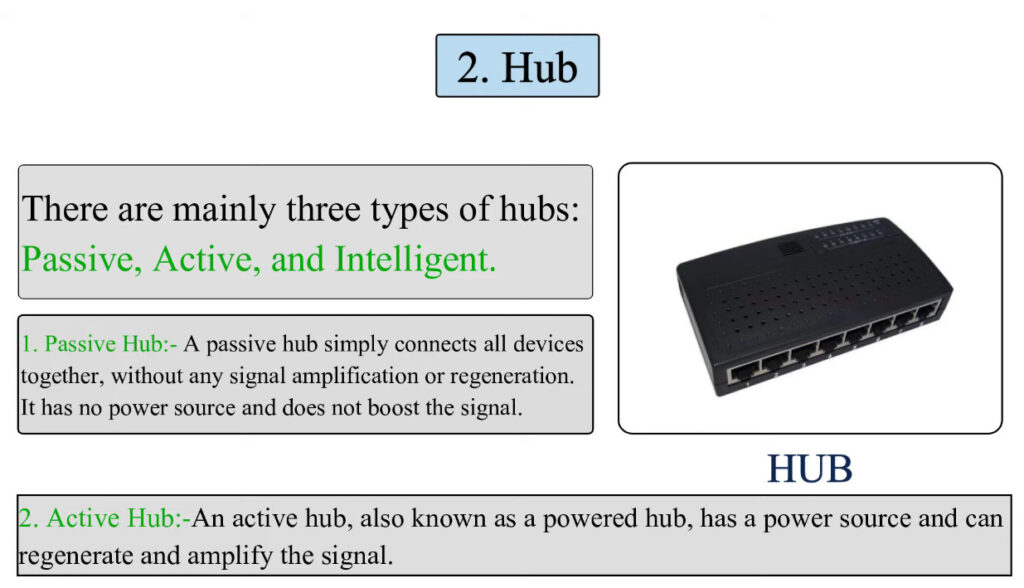
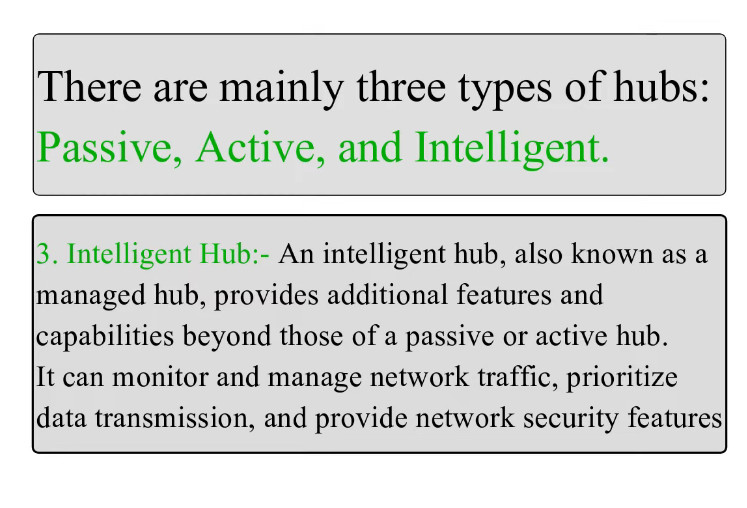
6. Hub
- A hub is an older network device that connects multiple devices in a LAN. It sends incoming data to all connected devices, even if the data is intended for only one device, which can create network traffic congestion.
7. Gateway
- A gateway acts as a bridge between different networks that use different communication protocols. It can translate data between different formats or protocols.
- For example, a gateway might allow communication between an internal network (e.g., an intranet) and the internet.
8. Firewall
- A firewall is a security device that monitors and controls incoming and outgoing network traffic based on predetermined security rules.
- It is used to protect the network from unauthorized access and cyber threats.
9. Modem
- A modem (short for modulator-demodulator) is used to connect a local network (LAN) to the internet via an ISP (Internet Service Provider).
- It converts digital data from a computer into analog signals for transmission over phone lines or cables.
10. IP Addressing and DNS (Domain Name System)
- IP Addressing: Each device on a network needs a unique identifier, typically an IP address (IPv4 or IPv6), to communicate with other devices.
- DNS: DNS translates human-readable domain names (e.g., www.example.com) into IP addresses so that computers can locate websites and services.
11. Protocols
- Protocols are a set of rules that determine how data is transmitted and received in a network. Some common network protocols include:
- TCP/IP (Transmission Control Protocol/Internet Protocol): The foundational protocol suite for the internet and most networks.
- HTTP/HTTPS (Hypertext Transfer Protocol): Used for transferring web pages.
- FTP (File Transfer Protocol): Used for transferring files between computers on a network.
- SMTP (Simple Mail Transfer Protocol): Used for sending emails.
12. Network Operating System (NOS)
- A Network Operating System (NOS) manages and controls the resources and devices in a network. It helps in configuring, managing, and monitoring the network. Examples include Windows Server, Linux, and macOS Server.
13. Wireless Access Points (WAP)
- In wireless networks, Wireless Access Points (WAP) provide a central point where devices can connect to the network. WAPs manage communication between devices and the wired network through radio signals.
14. Network Security Tools
- These include various software and hardware tools used to secure the network and data, such as:
- Antivirus software
- Encryption tools
- Virtual Private Networks (VPNs) to secure remote connections
15. Bandwidth and Speed
- Bandwidth refers to the maximum data transfer rate of a network or the amount of data that can be transmitted in a given amount of time. It is typically measured in Mbps (megabits per second) or Gbps (gigabits per second).
- Latency: The time it takes for data to travel from the source to the destination.
16. Cloud Services
- Many modern networks use cloud-based services to store data and host applications. The cloud allows for greater flexibility and scalability.
Summary of Key Components:
- Devices (Computers, Routers, Switches, etc.)
- Transmission Media (Ethernet cables, Wi-Fi, Fiber optics)
- Network Interface Cards (NICs)
- Router
- Switch
- Firewall
- Modem
- Gateway
- Protocols (TCP/IP, HTTP, FTP)
- IP Addressing and DNS
- Network Operating Systems (NOS)
- Wireless Access Points (WAP)
- Network Security Tools
- Bandwidth and Speed
- Cloud Services
Each of these components plays a critical role in enabling devices to communicate, share data, and ensure that the network operates efficiently and securely.